On January 25, Linus Torvalds submitted a prank README page to the Linux GitHub repository with a note called “delete linux because it sucks”.
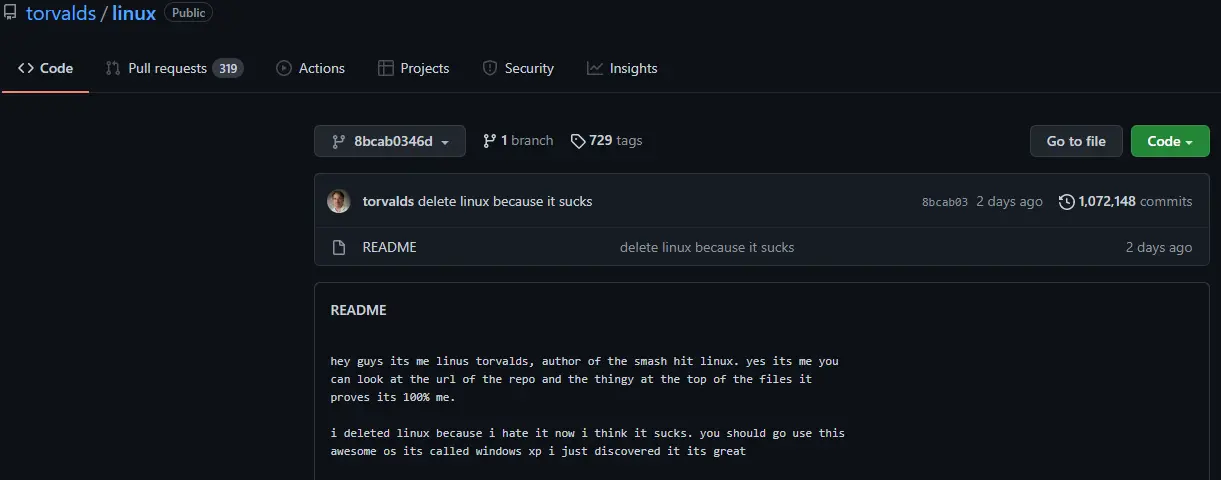
hey guys its me linus torvalds, author of the smash hit linux. yes its me you can look at the url of the repo and the thingy at the top of the files it proves its 100% me.
i deleted linux because i hate it now i think it sucks. you should go use this awesome os its called windows xp i just discovered it its great
Why is this a prank? Because the Linux source code has not been removed, and a careful observer noticed that there is a link at the bottom of the README.
This link leads to a Hacker News hacker forum thread detailing a “false commit” vulnerability that exists in GitHub: it is possible to post arbitrary commits under the https://github.com/my/project URL.
For example, with a URL like https://github.com/my/project/blob/<faked_commit>/README.md, you can post a fake README page that doesn’t appear in the project’s commit log and doesn’t belong to any branch, but can only be seen by visiting a specific URL. This prank README file from Linus exploits this false commit vulnerability, see the URL of this README.
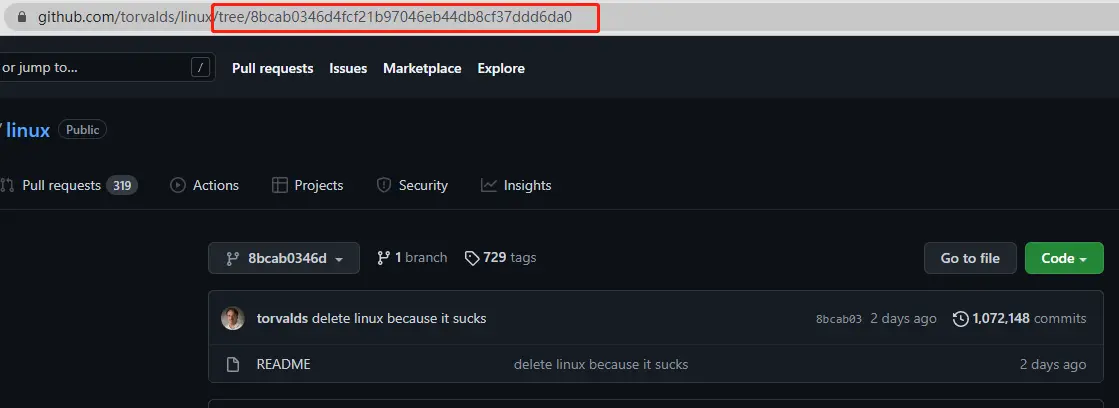
If it’s a normal commit, URL should have the word commit , for example.
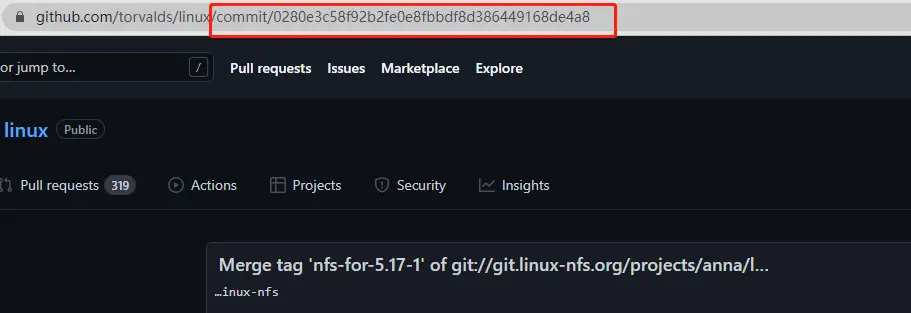
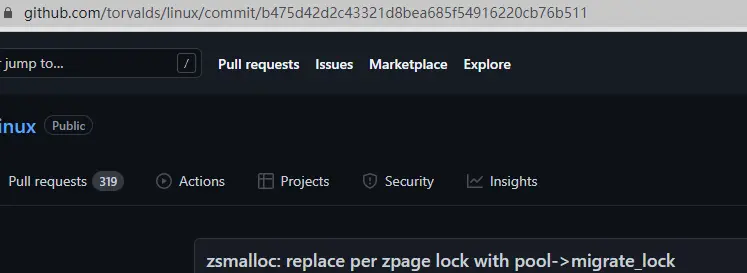
In addition to the URL not being external, the README file does not appear in the commit record.
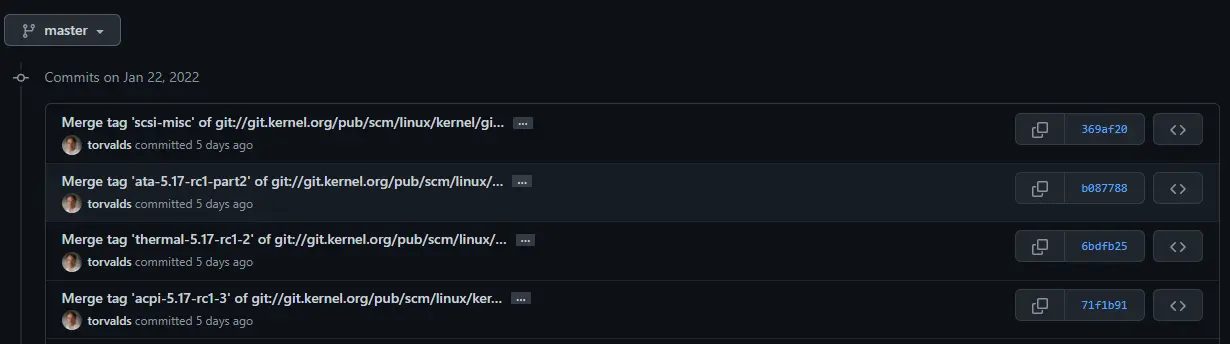
As you can see, Linus was just joking around and didn’t actually delete the repository.
If you’re interested in this vulnerability, check out the original Hacker News post about this fake commit vulnerability combined with another GitHub “impersonating a user through a git email address” vulnerability, can create fake phishing pages.
For example https://github.com/slimsag/linux/tree/5895e21f3c744ed9829e3afe9691e3eb1b1932ae#linux-kernel is a repository that looks as if Linus himself was involved in its construction.
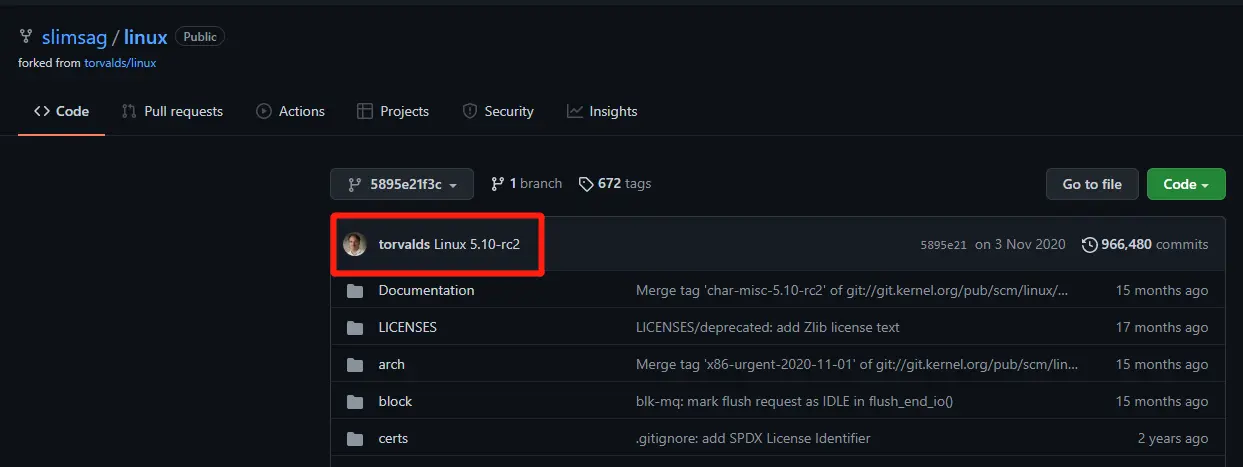
However, this is only done by replacing the email address vulnerability, replacing slimsag with torvalds.
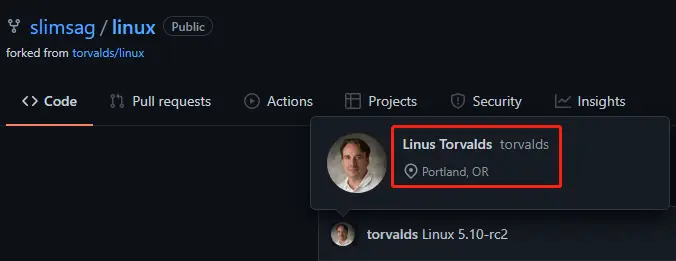
On the left are the torvalds with the email address replaced by the exploit, and on the right are the normal torvalds.
All of these GitHub vulnerabilities were made public in 2020, yet the authors of the vulnerabilities claim that “GitHub does not consider these issues as vulnerabilities at all”. I don’t know if GitHub couldn’t handle them, or didn’t think they needed to be handled, but they’re still exploitable to this day.