To talk about network protocols, we can’t leave the seven-layer model of OSI (Open System Interconnection). We generally focus on the layers above the network layer, such as IPV4 IPV6 in the network layer, TCP UDP in the transport layer, HTTP FTP in the application layer, etc.
Today’s sctp protocol, known as Stream Control Transmission Protocol, is proposed by the IETF in RFC 4960.
The transport layer has been widely used TCP and UDP protocols, so why do we have to invent a SCTP protocol?
It is clear that the SCTP protocol is an enhancement of the TCP and UDP protocols. Specifically, SCTP provides the message-oriented features of UDP protocol, while providing the reliability, sequential transmission and congestion control features of TCP protocol, and also provides multi-homing and redundant paths to improve resiliency and reliability.
This article will explain in detail the implementation principles and protocol details of SCTP.
What are the disadvantages of TCP?
What is wrong with TCP? TCP is certainly good, we know that UDP is an unreliable way of transferring messages, while TCP is a reliable way of transferring messages.
UDP and TCP have been used in a very wide range of applications. But a product or protocol can’t be perfect, there must be some drawbacks, let’s see what are the drawbacks of TCP.
The biggest difference between TCP and UDP is that TCP is reliable, which means that TCP provides a way to transfer data reliably over the Internet.
However, TCP imposes some restrictions on transmission in order to ensure reliable data transfer.
For example, TCP requires a strict order of data transmission in order to ensure the reliability of data transmission. For example, if a packet is split into three copies labeled A, B, and C, then for the receiver, packet A must be accepted first, followed by B and C. If B is accepted first, then the receiver will need to have the transmitter retransmit the packet.
With this strict packet order requirement, unnecessary data delays and message blocking may result.
Because TCP is stream-oriented, in order to mark different records in the data stream, the data in TCP needs some additional markers or encodings to differentiate the records.
In addition, in order to improve transmission efficiency and avoid sending multiple small packets, TCP may also optimize it, i.e., wait for multiple small packets to merge them into one large packet. If such optimization is not desired, then the PSH flag needs to be set in the TCP packet to make it clear that the request is a delay-free transmission request.
Finally TCP is also vulnerable to DOS (denial-of-service) attacks.
Features of sctp
Since TCP has many drawbacks, what are the features of the new SCTP protocol?
SCTP has two main features, the first one is Message-based, which means that SCTP is message-oriented. sctp transmits a series of messages, and a message is a set of bytes.
In contrast, TCP transmits a stream of bytes.
A message in SCTP can be split into multiple data blocks, with all the data in each block coming from the same user. When these data need to be transmitted in IP, SCTP will packetize these packets into SCTP packets, each SCTP packet contains a packet header, a control block if needed, and finally a data block.
How to understand the difference between TCP packets and SCTP packets?
As an example, when a client sends multiple messages to the server side using TCP protocol, if the messages are very short, TCP may put these small data with different roles into the same TCP packet in order to improve transmission efficiency. All the data in this TCP packet is also received at once during the reception on the server side, and then the application itself performs the splitting of the underlying data in the TCP packet.
For SCTP packets, one SCTP packet can contain multiple data chunks, and different data chunks can contain different messages from different users, because SCTP packets already differentiate different messages, so it is relatively easy for the server side to read them.
The following is the basic structure of an SCTP package.
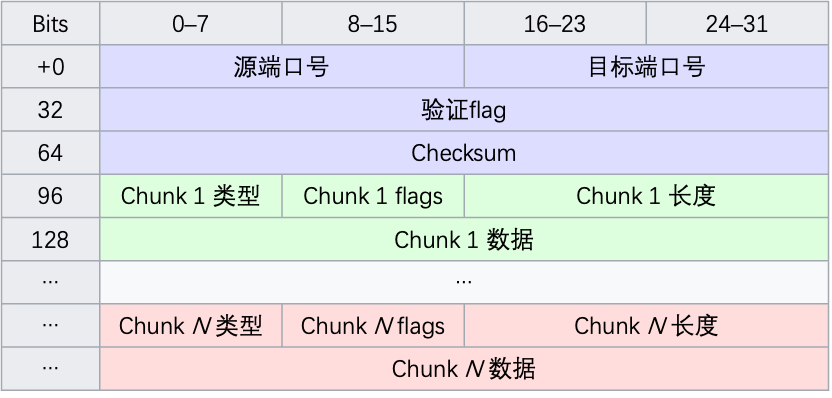
From the above figure, we can see that the 12 bytes in the front blue part are the packet header of SCTP packet, in which the first two bytes are the source port number, followed by the next two bytes are the target port number, then 4 bytes are the authentication marks, and the last 4 are the check bits directly, totaling 12 bytes.
After the header is the data chunks, that is, the data chunks, each chunk contains a type bit, flags bit and length bit, followed by the specific data of the chunk.
Another feature of SCTP is multi-streaming, which means that SCTP can transmit multiple independent data streams in parallel, such as images and text of a web page when accessing a web page.
Why is this possible? This is also determined by the structure of SCTP packets. We can see that SCTP packets can contain multiple data chunks, which can contain data from different data streams, so the message-oriented SCTP can realize the function of parallel transmission of data from different data sources.
Another feature of SCTP is Multihoming, Multihoming is a composite word of multiple+homing, which literally means multiple home.
From the above figure, we can see that the 12 bytes in the front blue part are the packet header of SCTP packet, in which the first two bytes are the source port number, followed by the next two bytes are the target port number, then 4 bytes are the authentication marks, and the last 4 are the check bits directly, totaling 12 bytes.
After the header is the data chunks, that is, the data chunks, each chunk contains a type bit, flags bit and length bit, followed by the specific data of the chunk.
Another feature of SCTP is multi-streaming, which means that SCTP can transmit multiple independent data streams in parallel, such as images and text of a web page when accessing a web page.
Why is this possible? This is also determined by the structure of SCTP packets. We can see that SCTP packets can contain multiple data chunks, which can contain data from different data streams, so the message-oriented SCTP can realize the function of parallel transmission of data from different data sources.
Another feature of SCTP is Multihoming, Multihoming is a composite word of multiple+homing, which literally means multiple home.
What does this mean?
We know that for the TCP protocol, there is only one client and one server, which is a one-to-one connection, and if any IP or port at both ends of the connection is not available, then the whole TCP connection will collapse.
So can TCP be developed into a model similar to LSB load balancing? If an IP does not work, it automatically reconnects to an alternate IP address.
SCTP is an upgraded version of the TCP protocol that is optimized for enhanced reliability.
Specifically, each SCTP node uses a heartbeat mechanism to regularly check the reachability of the remote node’s primary IP address and the alternate redundant IP address. A node can be bound to multiple IP addresses in SCTP.
The SCTP node will confirm the specific access information based on the heartbeat return value received from the remote node.
Since the number of client-side and server-side nodes may be different, SCTP can be divided into symmetric multihoming and asymmetric multihoming.
The following three figures show the symmetric multihoming and two asymmetric multihoming cases respectively.
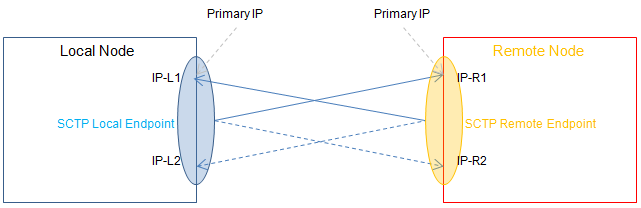

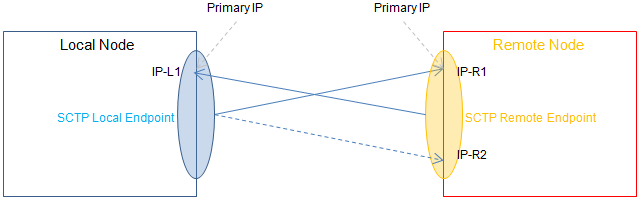
Finally, the security of SCTP has been improved. Compared to TCP’s three handshakes, SCTP has four handshakes.
TCP’s three handshakes can lead to SYN attacks.
What is a SYN attack? First, the client sends a SYN A request to the server side. After receiving this SYN request, the server side caches the SYN request and returns SYN B, ACK A+1, to the client side, which checks the ACK value after receiving the reply and then sends ACK B+1 to the server side again. After the server side receives the B+1 request, it finally confirms the identity of the client and the connection is established.
In the above process, since the server side needs to cache the SYN messages of TCP clients, if the server receives a large number of SYN messages, it will cause a SYN attack.
In contrast, SCTP does not immediately allocate memory to cache the client’s connection request after receiving it, but returns a COOKIE to the client. When the client requests again, it needs to bring this COOKIE information, and the server will confirm the identity of the client through COOKIE verification before finally establishing the connection. This avoids TCP SYN attacks.
Summary
In summary, SCTP can ensure the reliable transmission of ordered and numerous data streams, can support Multihoming, and each node can contain multiple IP addresses, thus enabling transparent failover between redundant network paths. It also enhances the verification and validation mechanism, which can prevent SYN attacks.
SCTP is an excellent protocol. For common operating systems, support for SCTP is also provided in specific versions. For example, in linux, the SCTP protocol is supported above kernel version 2.4.
If you are using SCTP on windows or MAC, you need to install additional third-party drivers, which are called SctpDrv kernel driver for windows and SCTP Network Kernel Extension for Mac OS X for MAC.