firewalld in CentOS is built on iptables and some other programs. firewalld uses some more friendly configuration methods to implement iptables operations. It also extends some features that are not supported by iptables itself, such as timed firewall rules. The full program and library dependencies are available on the firewalld website at https://firewalld.org/.
iptables processes network packets by manipulating the Linux kernel netfilter module.
Please temporarily disable the firewalld firewall on your machine before operating the command, and make sure you have access to the physical machine (or a physical terminal in a virtual machine), as some rules will block access to SSH port 22 and prevent subsequent operations.
iptables basic concepts and operations
Policy Chain
The iptables filtering rules are used to determine the processing of packets in different situations by matching the rules in a policy chain, which contains three policy chains.
- INPUT : This chain is used to control incoming connections and packets, such as allowing SSH incoming connections from certain IPs.
- FORWARD : Forwarding control link, this chain is used if you need to configure routing features on the machine.
- OUTPUT : Outgoing chain, this chain is matched when the current host sends a request to the outside, and usually no special rules are configured for it when there is no special need.
You can view the currently set iptables rules with the following command.
Policy Chain Default Behavior
The corresponding policy chain will have a default behavior. It means that the chain is defined to handle packets when it does not match any rule.
Use the following command to view the behavior of the current policy chain (the number of packets and traffic not matching this chain are also output).
If the current policy chain does not behave as shown above, the following command can be used to set the behavior of accepting all data.
The following command can be tried to discard packets in all cases.
Note: At this point, the external host will not be able to access the host, and the internal host will not be able to access the external.
Response of the chain
With the default policy chain in place, custom rules can be added. When matching a rule that matches the requirements (e.g. target port/source of data) how you want the data to be processed.
The following three “responses” are commonly used for chaining
- ACCEPT : All connections and data are allowed.
- DROP : Drops the connection. The sender will be unaware, as if the host does not exist.
- REJECT: Connection is rejected and an error message is returned. The sender will know that the request was blocked by the firewall.
The behavior of the peer machine configured with different INPUT policy chains can be tested with the ping command.
ACCEPT:
|
|
DROP:
REJECT:
Strictly speaking, ACCEPT and DROP are the target of the chain, while REJECT is the target extension, so REJECT cannot be configured for chains, only REJECT rules can be added to chains.
Chain rules
Once the chain is configured, rules can be added to it. For adding a rule, use a command of the following form.
|
|
The targets include custom chains in addition to the ACCEPT/DROP/REJECT mentioned above, as well as other extended targets.
Before attempting to follow up, keep in mind the following command to reset the firewall.
drops all ICMP protocols
External pinging of the current host will prompt a timeout. The current machine will not be detected when using the traceroute command for route tracing.
|
|
Allowed connection ports only
Configure the INPUT policy chain to default to DROP first and then configure allow rules for it.
discards data from a specified source
Data from a fixed IP can be specified to be discarded.
|
|
Or, to discard all data under the source segment.
|
|
Custom Chains
Chains can be created, and custom chains can be added to INPUT policy chains after adding rules using the following command.
After the addition is complete the configuration is:
|
|
You can see that the default behavior of the INPUT policy chain is ACCEPT, with an arbitrary matching rule targeting mychain.
So when matching input data, all data tries to match mychain’s rules.
In mychain, if the matching protocol is ICMP, the data is discarded.
Save and Restore
If you do not execute the command to save the configuration, all changes will be discarded after a system reboot.
Use the iptables-save command to save changes to take effect after a reboot and output the configuration save command.
Use iptables-restore to read in the configuration from standard input and restore it.
firewalld Basic Concepts and Operations
Make sure firewalld is started before operating it.
Network zones (ZONE)
The firewall presets a number of network zones, and the system assigns network interfaces to public zones by default.
The firewall preset configuration files are defined in the /usr/lib/firewalld/zones directory, and the user-defined files are in the /etc/firewalld/zones directory. The detailed policy and format can be found in firewalld.zone(5), or see the linked article at the end of this article.
In the initial state, the firewall-cmd -list-all command allows you to get the status of the default network zone public.
To modify the default network zone, edit the DefaultZone field in the /etc/firewalld/firewalld.conf file.
Use firewall-cmd -list-all-zones to display all network zone configurations.
Open ports
You can open the port by direct command, please use reload command to reload the firewall configuration after the configuration is done.
Port access can be removed using the corresponding remove-port command.
Please note: To set permanent settings, add the -permanent option, which will be added to all relevant firewall commands below without exception.
Open ports by configuring the service file.
In the initial configuration, only two services, dhcpv6-client and ssh, are open for external access in the public network area of firewalld. They are exposed on ports 546/udp/ipv6 and 22/tcp.
A set of service configuration files described in XML is defined in the /usr/lib/firewalld/services directory.
|
|
Copy the SSH service as a template to the user configuration directory. and modify port 22 to 8080, the contents of the file are as follows
The next step is to open the port by means of a service.
A simple HTTP server can be started in Python to test whether port 8080 is open.
Forwarding Port
By configuring the forwarding port, you can forward the data accessing the specified port to other specified host ports, here is the example of the current host, forwarding all accesses to port 8080 to 8081.
The preceding Python command starts an HTTP server with port 8081, at which point external access to the data on port 8080 of the current host will be able to access the content directly.
The corresponding command to remove forwarding is also
Rich Language
Use Rich Language to create relatively complex rule configurations, such as restricting tcp port 8080 under ipv4 to be accessed only by the 10.1.1.0/2 network segment.
Rich Languange is an abstract representation of the iptables utility.
The full format description can be found in firewalld.zone(5), but in XML format.
firewalld and iptables
All tables of iptables
Before discussing firewalld in relation to iptables, it is important to briefly understand all the tables in iptables.
iptables supports five tables to provide configuration in various environments.
filter table
The default table with three built-in chains: INPUT (for packets destined for local sockets), FORWARD (for packets routed through the local machine), OUTPUT (for locally generated packets).
nat table
This table is queried when packets are encountered for creating new connections. It contains three built-in chains: PREROUTING (for modifying packets as soon as they come in), OUTPUT (for modifying locally generated packets before routing), and POSTROUTING (for modifying packets before they come out).
NAT support for IPV6 from Linux kernel version 3.7
mangle table
This table is dedicated to packet modifications. Until Linux kernel 2.4.17 only two chains were supported: PREROUTING (for modifying incoming packets before routing) and OUTPUT (for modifying locally generated packets before routing). Starting with kernel 2.4.18, three additional chains are supported: INPUT (for sending to the local machine before), FORWARD (for routing packets through the local machine), and POSTROUTING (for modifying data before the packet is passed out).
raw table
This table is primarily used to configure exemptions from connection tracking in conjunction with the NOTRACK target. It has a higher priority for netfilter hook registration and is invoked before ip_conntrack and any other IP table. It contains two chains: PREROUTING (for packets arriving through any network interface), and OUTPUT (for any packets generated by the local program).
security Table
Used for Mandatory Access Control (MAC) network rules. It is a security policy, not discussed in detail in the text, which contains two chains: INPUT / OUTPUT.
The order of the call chains between the regular tables.
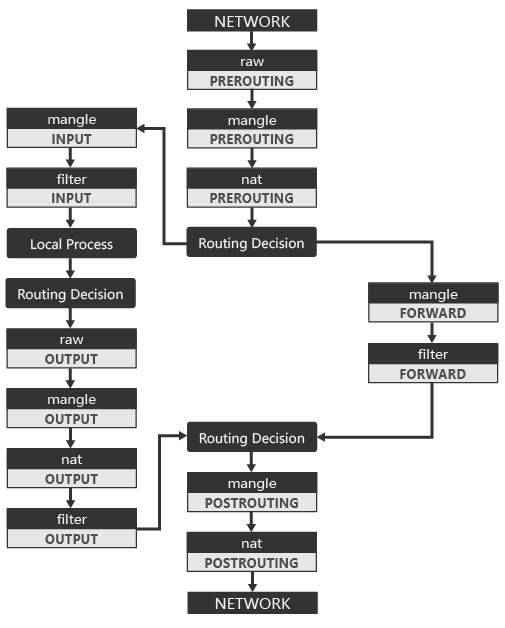
filter table basic policy
When the firewalld firewall is in its initial state.
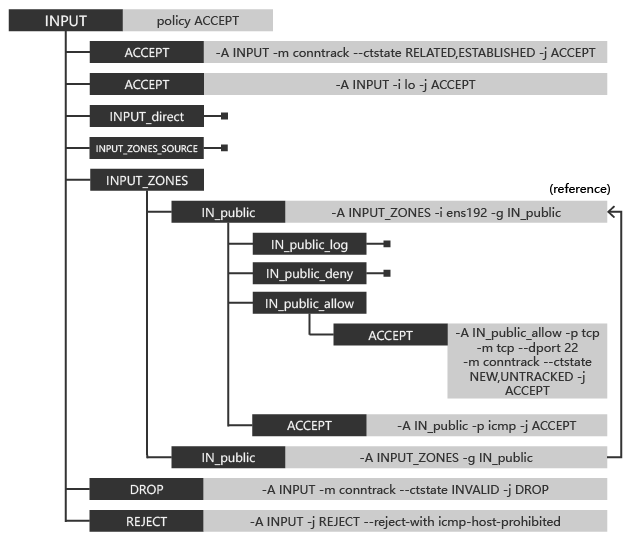
INPUT chain
|
|
It first accepts all established connections, as well as all data from the lo network interface (local loopback).
The two custom chain rules with target INPUT_direct / INPUT_ZONES_SOURCE are empty and reserved for specific firewalld configuration functions.
The INPUT_ZONES target contains the configuration of the network zone under.
|
|
The INPUT_ZONES chain contains chains named IN_<network_zone>, which will also match the network interface. The default network zone will be the last matching rule.
IN_public contains four rules, adds three chain targets: IN_public_log / IN_public_deny / IN_public_allow, and accepts all ICMP requests. The IN_public_log / IN_public_deny rule is empty and reserved for specific functions.
The actual pass rule is contained in IN_public_allow, which allows port 22.
|
|
At the end of the chain of INPUT, if no rule is matched, all invalid packets are discarded and all other requests are rejected.
FORWARD chain
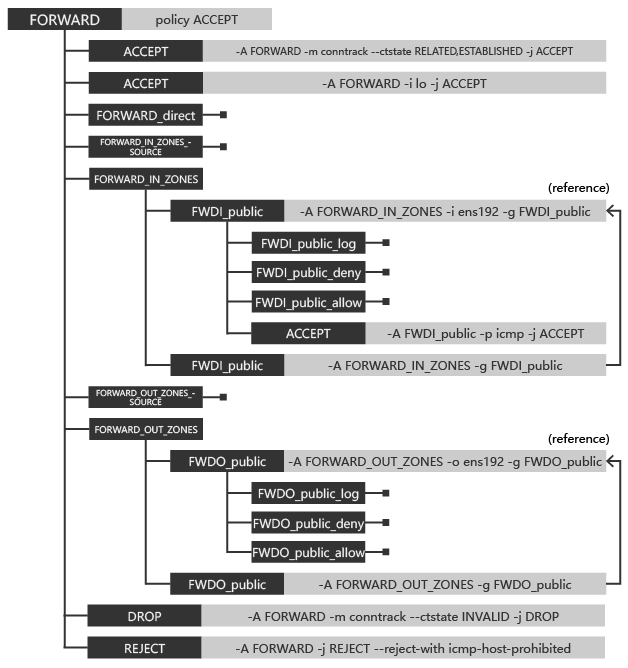
The FORWARD chain is very similar to the INPUT chain in the filter table, except that for network zones, custom chains are distinguished between IN and OUT.
|
|
In the FORWARD_IN_ZONES chain, match all input data from the web interface.
|
|
In the FORWARD_OUT_ZONES chain, match all outputs to the web interface for all data.
|
|
However, under the initial firewalld configuration, all data under the FORWARD chain is discarded or rejected except for the match in FWDI_public to allow incoming ICMP protocols from the ens192 network interface.
OUTPUT chain
The rules for the OUTPUT chain are simple.
|
|
For local loopback data pass directly, otherwise match the OUTPUT_direct link used for the rule configuration of firewalld, with an initial rule of null. If not matched, then use the policy ACCEPT for the OUTPUT chain to allow all data to pass.
firewalld add port policy
Add ports directly in firewalld via services or commands, and via Rich Language as well.
It will be added directly to IN_public_allow:
|
|
Alternatively, the table and chain of iptables can be specified using firewalld’s direct add rule command.
|
|
It can also be added directly to the INPUT_direct table, which will match rules before the network zone chain INPUT_ZONES.
nat table basic policy
PREROUTING and POSTROUTING chains
The PREROUTING / POSTROUTING chain in the nat table has a similar configuration policy to the INPUT chain in the filter table, and only PREROUTING is listed here.
|
|
INPUT and OUTPUT chains
The default configuration provided by firewalld in the nat table is simple.
firewalld add port forwarding policy
The preceding port forwarding configuration is an example.
firewalld adds the following rules to each of the mangle and nat tables.
The mange table marks all packets from port 8080/tcp in the PREROUTING phase with a 0x64/0xffffffff, the former being the value and the latter being the mask. The result is heterogeneously added to ctmark. ctmark is a 32-bit marker value provided by netfilter.
Adds a packet to the nat table that matches the 0x64/0xffffffff ctmark value if successful and adds it to the DNAT destination. Specify the destination parameter as forwarding to local port 8081.
DNAT targets can only be used in the PREROUTING and OUPUT chains in the nat table and the associated call chains.
Alternatively, try configuring iptables directly for port forwarding without starting firewalld.
Ending
This article briefly describes the basic operation and configuration of iptables and firewalld in CentOS as a test environment.s
firewalld can configure iptables at a high level of abstraction, for example by internally maintaining a ctmark value for port forwarding.
For port openings that do not specify an ip protocol version, firewalld maintains both ipv4 and ipv6 configurations, which can be viewed separately with the following command.
There are tools similar to firewalld in other Linux distributions, and iptables is present in most distributions.