The Linux network stack is very efficient and at the same time complex. If we want to do something with the data we care about during the processing of the data, how can we do it?Linux provides a mechanism to implement custom packet processing for the user.
There is a set of callback function hooks in the Linux network stack, through which hooks can be attached to the Linux network stack to perform some operations on the packet during processing, such as filtering, modifying, dropping, etc. The whole hook point technology is called Netfilter and iptables.
Netfilter and iptables are not two separate components; Netfilter is a firewall framework in kernel space, while iptables can be thought of as a client in user space.
Netfilter’s core functions are packet filtering, packet modification, network address translation (NAT)
Basic Concepts
Rules concept
The core concept of iptables is Rules, i.e. rules, which in one sentence sums up its working logic as “execute pre-specified logic for packets that match the rules”. There are several concepts involved here, the first is matching, which is well understood, that is, to see if it matches. For iptables, it deals with packets, so it naturally matches information related to packets, such as source address, destination address, transport protocol, service type, and only when these can be matched, it executes some rule logic, such as release, deny, discard, etc.
Five chains
Maybe you are not familiar with what iptables does and how it works, but when you hear an insider talk about iptables, he will definitely mention “four tables and five chains”, so what are the four tables and no chains of iptables? And what do they do?
First of all, “chain”, the chain here refers to the “rule chain”, that is, in the work of iptables, not only through a rule to deal with packets, but there are many rules, these rules are arranged in a certain order, the message When passing through iptables, we have to match some rules one by one to perform the corresponding action, we regard this series of rules as a kind of string, which is called “chain”.
For example, one of the chains called PREROUTING, its internal structure is like this.
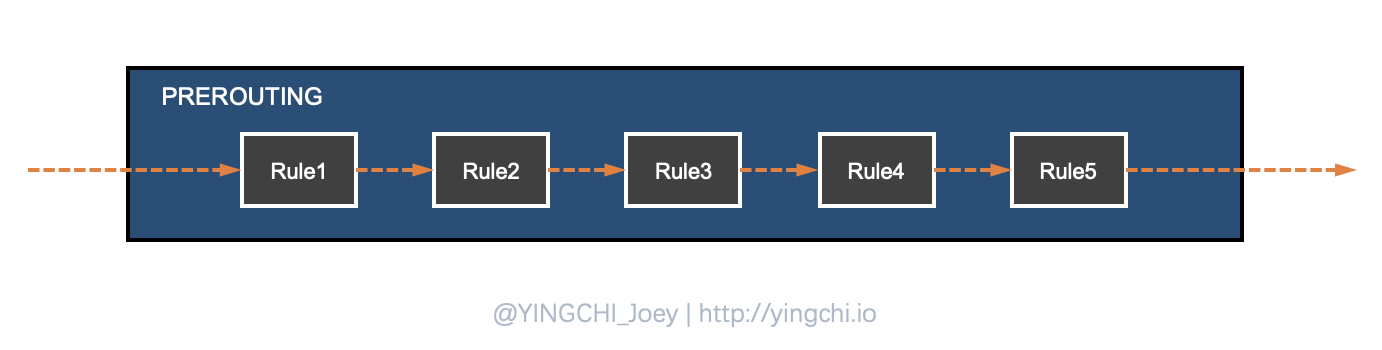
The packet will go through many rules matching in this chain. If the packet does not match any of the rules in the chain, iptables will process the packet according to a predefined default policy.
There are five chains in iptables as follows.
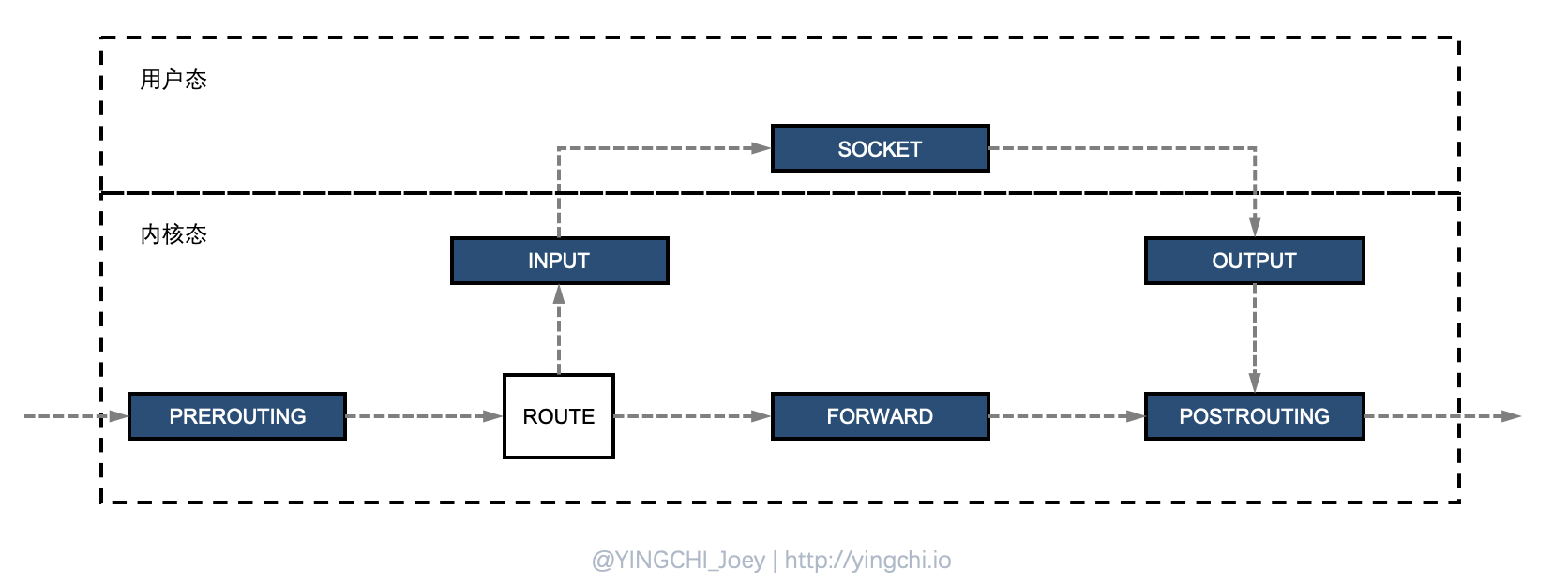
- PREROUTING chain: before routing.
- INPUT chain: routing destination local.
- FORWARD chain: routing destination non-local, forwarding.
- OUTPUT chain: packets sent by the local machine.
- POSTROUTING chain: after routing selection.
Four tables
After knowing the five chains, the next look at the four tables, if the chain is the performance of a series of rules to perform the sequential relationship, then the table is a series of rules to perform the functional logic relationship, we the same function of the collection of rules called “table”, because we will find that sometimes in different chains of the implementation of the rules between them Because we find that sometimes rules executed in different chains are intrinsically related to each other, or to the filtering of data, or to the modification of message data, etc., iptables provides us with the following classification of rules.
- Filter table: iptables default table, responsible for packet filtering, firewall functionality.
- NAT table: responsible for the network address translation function, corresponding to the kernel module.
- Mangle table: mainly responsible for modifying packets, corresponding to the kernel module.
- Raw table: highest priority, disables the connection tracking mechanism enabled by the NAT table.
Note that these tables are prioritized, from high to low priority: raw->mangle->nat->filter
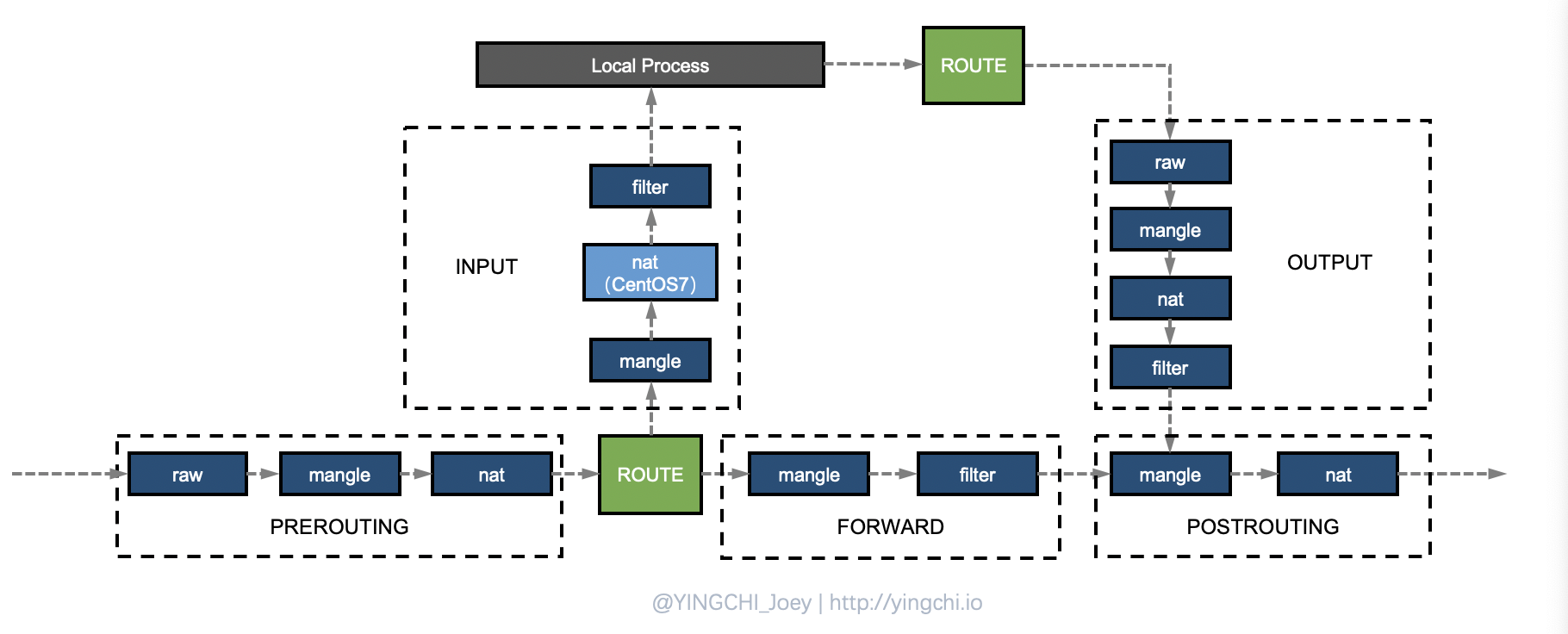
The correspondence between chains and tables is not casual either. Some table rules may exist only on the corresponding chains, and the specific correspondence is as follows.
PREROUTING chain: raw table, mangle table, nat table.
INPUT chain: mangle table, filter table, (centos7 can also have nat table)
FORWARD chain: mangle table, filter table.
OUTPUT chain: raw table mangle table, nat table, filter table.
POSTROUTING chain: mangle table, nat table.
Look at the rules again
The concept of rules was only mentioned at the beginning, so how should the matching and rule logic of rules be defined and carried out?
Matching conditions
There are basic matching conditions and extended matching conditions
- Basic matching condition: source IP, target IP.
- extended matching conditions: in addition to the above conditions that can be used for matching, there are many other conditions that can be used for matching, which are generically called extended conditions, such as source port, destination port, etc.
rule logic
Rule logic is called target in iptables, and some of the common processing logic is as follows.
- ACCEPT: allowing packets to pass.
- DROP: discard packets directly.
- REJECT: deny packets.
- SNAT: source address translation, which can solve the problem of intranet users using the same public address to access the Internet.
- DNAT: destination address translation.
- MASQUERADE: a special form of SNAT for dynamic, temporarily changing ip’s.
- REDIRECT: port mapping on the local machine.
- MARK: packet marking.
Notes.
- destination address translation generally operates in the PREROUTING chain
- source address translation is generally operated in the POSTROUTING chain
Summary
- when the host receives a packet, the packet is first processed in the kernel space, and if the destination address is found to be itself, it is passed to the corresponding application in user space, and if the destination is found not to be itself, the packet will be discarded or forwarded.
- iptables to achieve the firewall function is the principle: in the packet through the kernel process there are five key places, respectively PREROUTING, INPUT, OUTPUT, FORWARD, POSTROUTING, the user can write rules in these five chains, the packet through the processing, the general definition of the rules The rules are generally defined as “if the packet header meets such a condition, process the packet this way”.
- There are 5 chains defined in iptables, and multiple Rules can be defined in each chain. Whenever a packet reaches a chain, iptables will start matching from the first rule in the chain to see if the packet meets the conditions defined by the rule. If it does, the system will process the packet according to the rule logic defined by the rule (called target); otherwise iptables will continue to check the next rule, and if the packet does not meet any of the rules in the chain, iptables will process the packet according to the pre-defined default policy;.
- There are tables defined in iptables, which indicate the functions provided, respectively, the filter table (to achieve packet filtering), nat table (to achieve network address translation), mangle table (to achieve packet modification), raw table (to achieve data tracking), and these tables have a certain priority: raw->mangle ->nat->filter