The previous article focused on understanding the basics of cryptography, including the principles of the two encryption algorithms, and ended with the introduction of the concept of Digital Certificate in asymmetric encryption algorithms. This note will continue to explore what a digital certificate is, but before we can understand it, we must first know what a digital signature is.
There is a very classic article that describes the concept of digital signatures and digital certificates in detail, and most of this article is taken from that article.
Digital Certificates and Digital Signatures
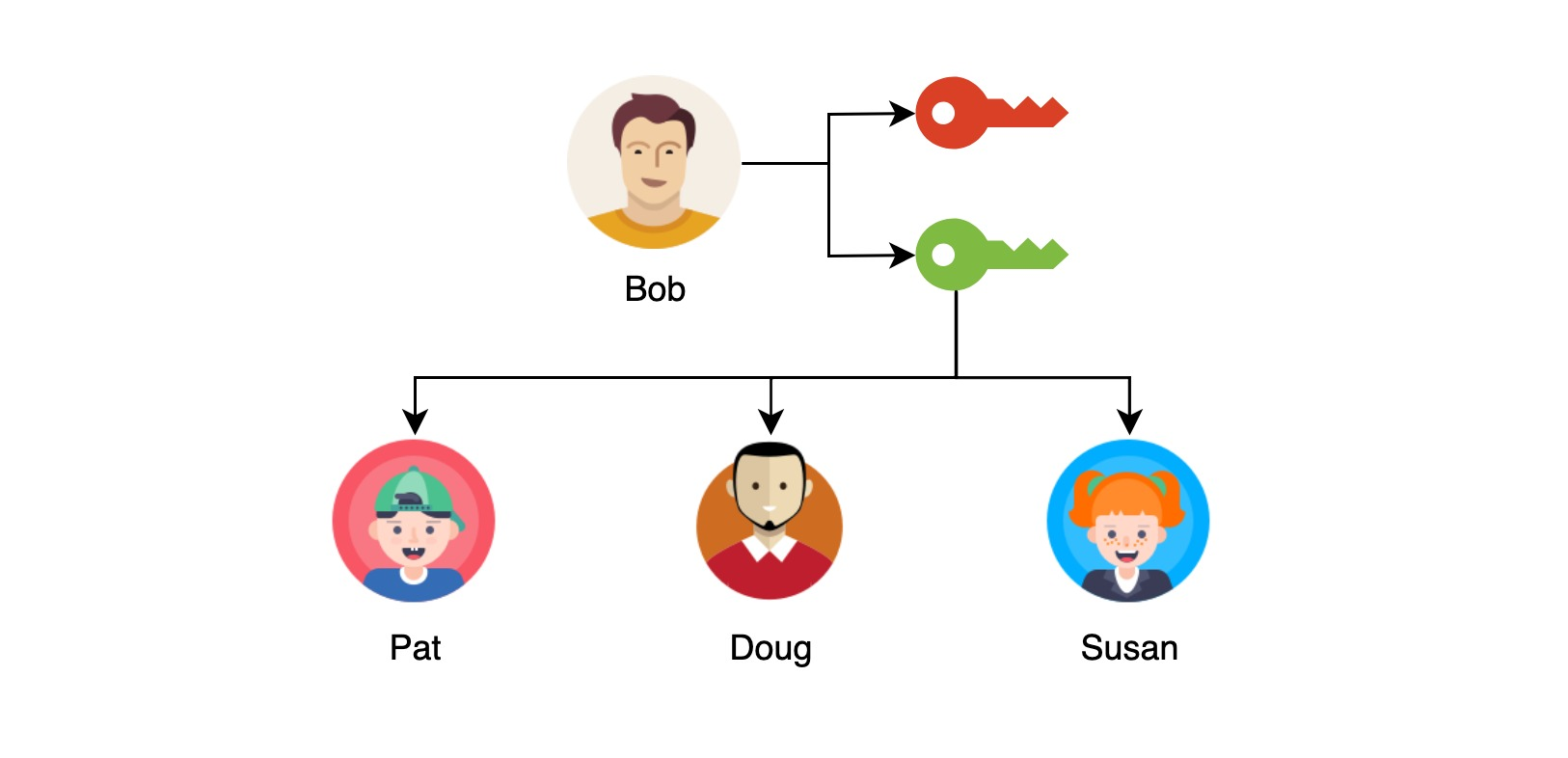
Bob generates his own public and private key pairs, keeps the private key for himself, and distributes the public key to his friends: Susan and Daug
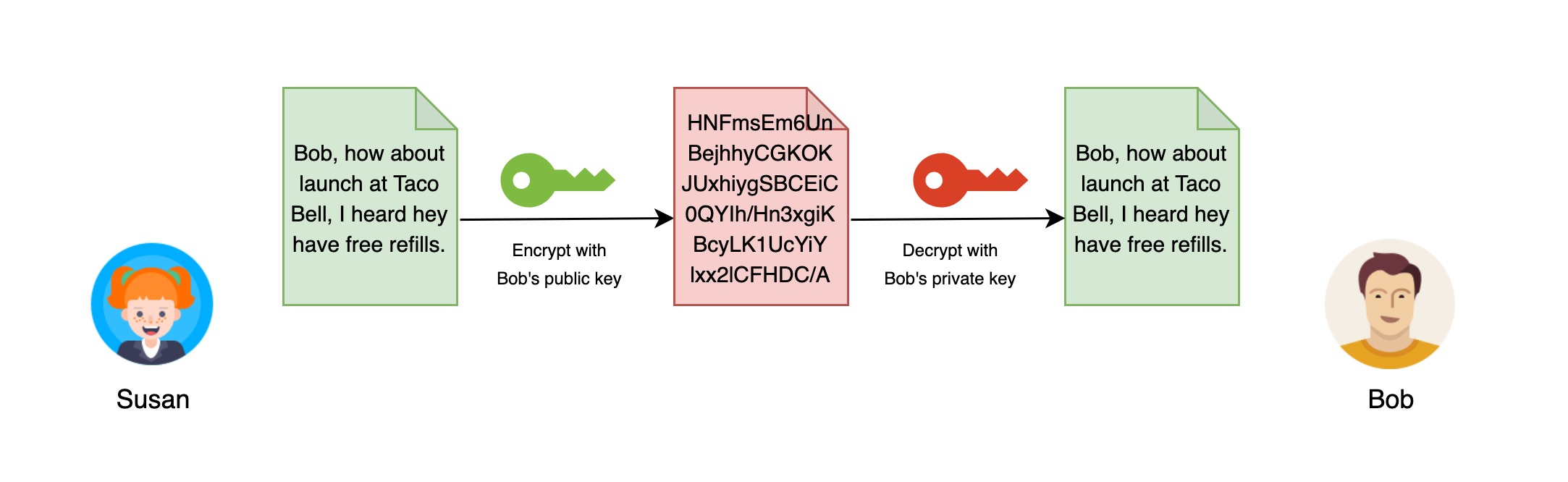
Susan wants to write a confidential letter to Bob, and encrypt it with Bob’s public key after writing. After Bob receives the letter, he decrypts it with his private key and can see the contents of the letter. Assuming that Bob’s private key is not leaked (private key is very sensitive information and must be kept carefully), even if the letter is intercepted by others, the contents of the letter cannot be decrypted, which means that no third person will know the contents of the letter.
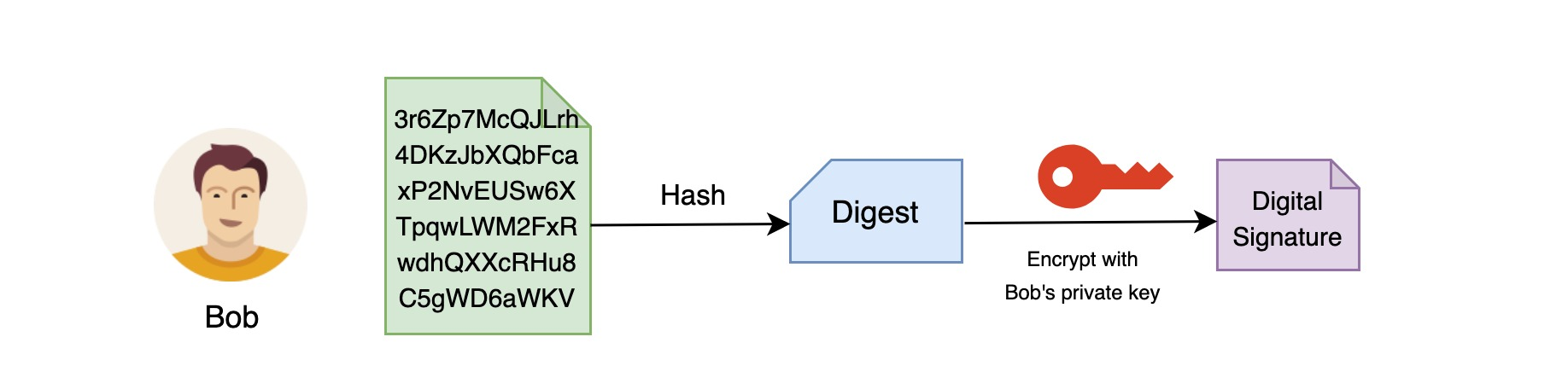
Bob writes a letter to Susan and decides to use a “digital signature”: after he writes the letter, he first uses a hash function to generate a digest of the letter and then, using his private key, encrypts the digest to generate a “digital signature”.
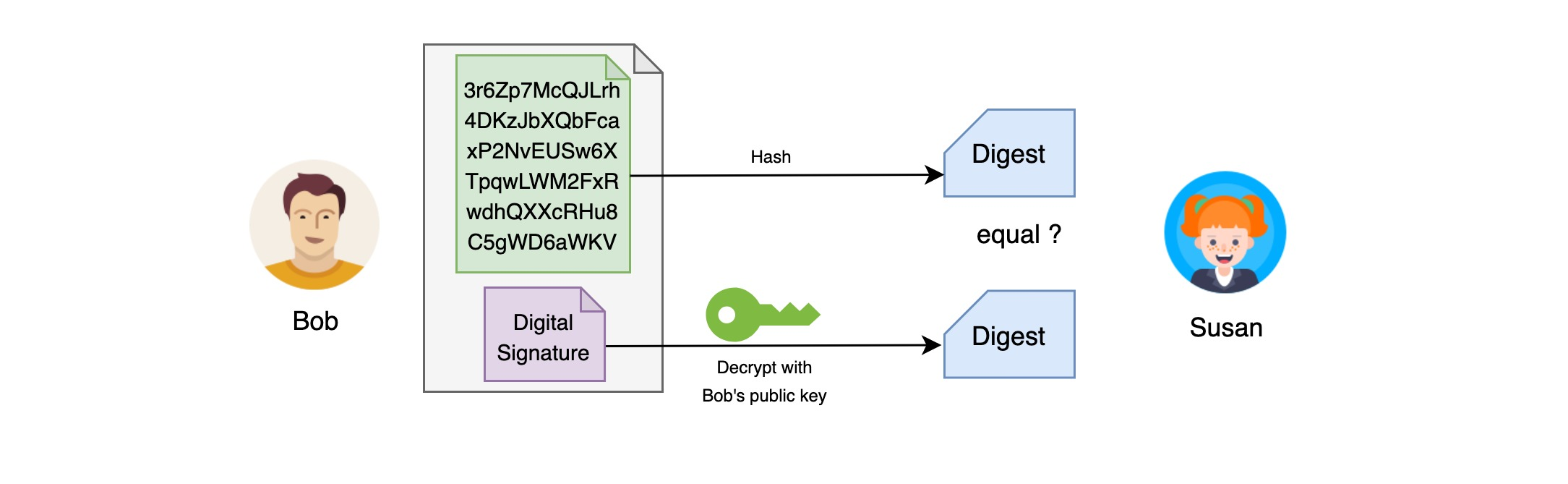
Bob sends this digital signature, attached to the letter, to Susan together.
After Susan receives the letter, she uses the same hash function on the letter itself to get the digest of the current letter, and at the same time, she takes down the digital signature and decrypts it with Bob’s public key to get the digest of the original letter, if the two are the same, it means that the contents of the letter have not been modified. This proves that the letter is indeed sent by Bob.
However, a more complicated situation arises. Daug wants to deceive Susan by making a pair of public and private keys disguised as Bob and distributing the public key to Susan, who actually keeps Daug’s public key but thinks it is Bob’s public key. Therefore, Daug can impersonate Bob and use his private key to make a “digital signature” to write to Susan, who uses the fake Bob public key to decrypt. Everything looks perfect?
Susan thought something was wrong because she wasn’t sure if the public key really belonged to Bob. So she comes up with a solution and asks Bob to go to the Certificate Authority and have the public key certified. The certificate authority uses the private key of the certificate authority to encrypt Bob’s public key and some related information together to generate a Digital Certificate.
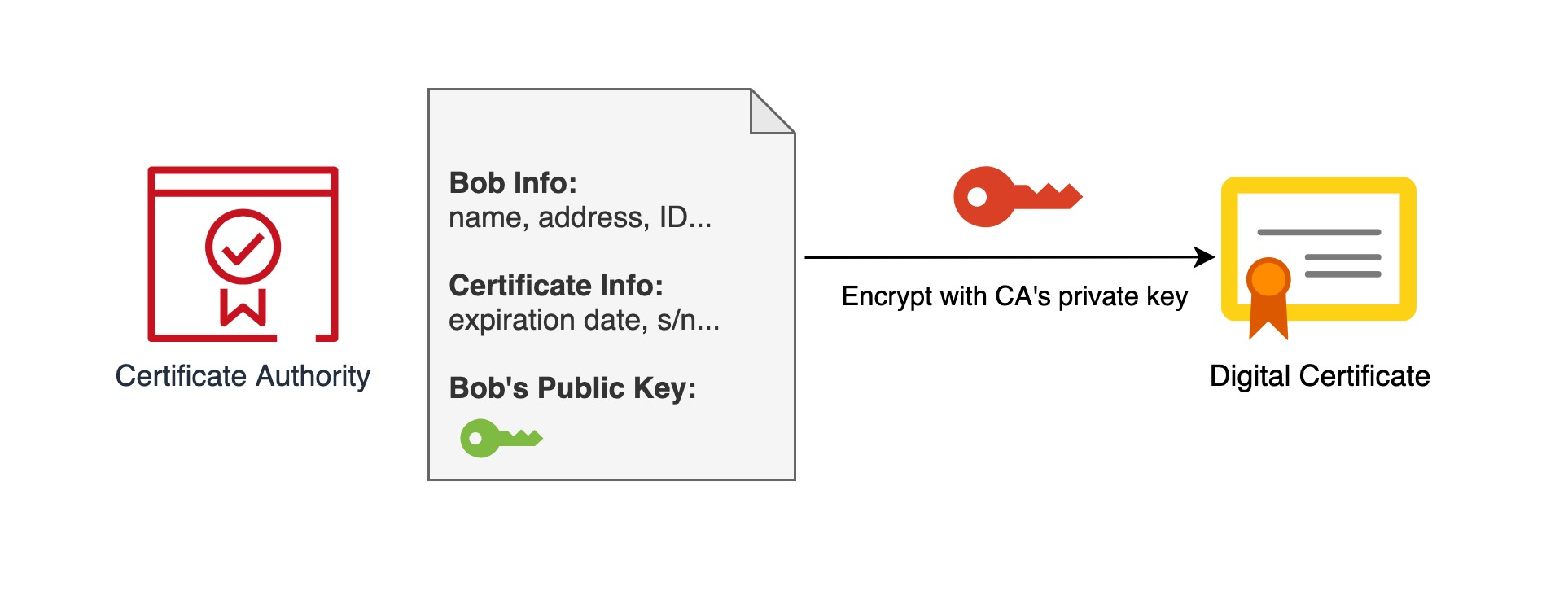
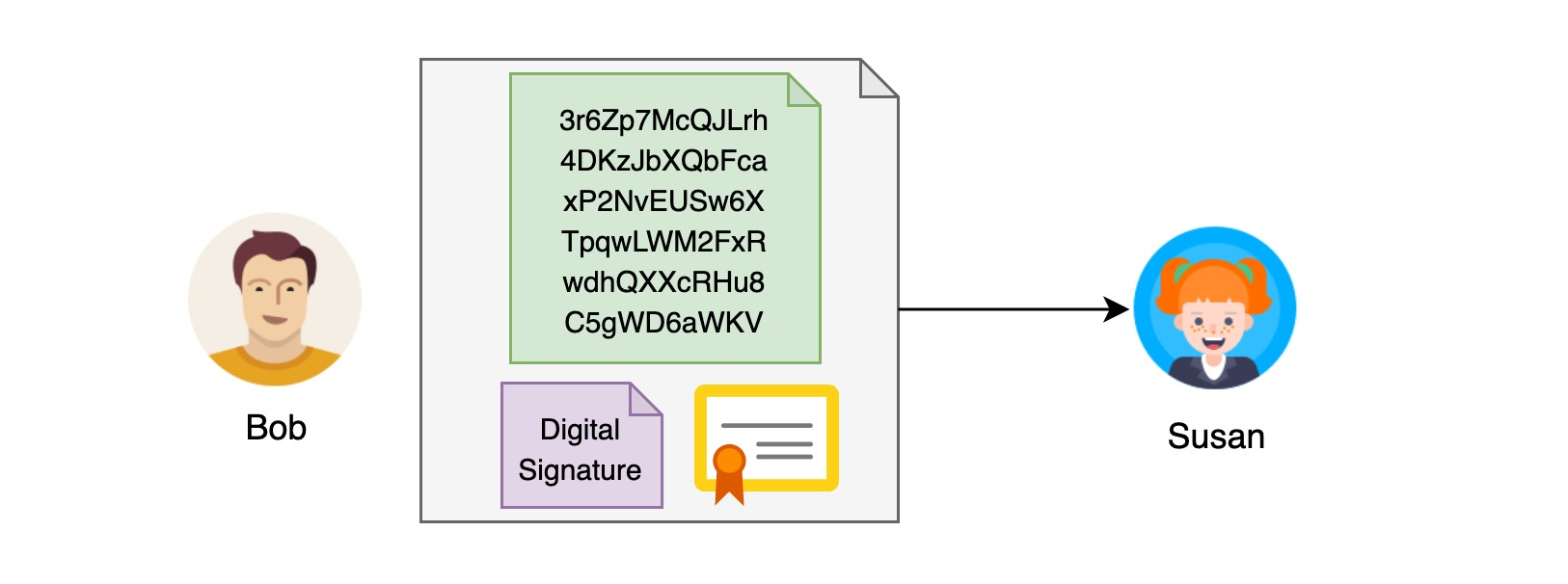
Once Bob has the digital certificate, he can write to anyone with confidence. All you need to do is attach the digital signature to the back of the letter and the digital certificate.
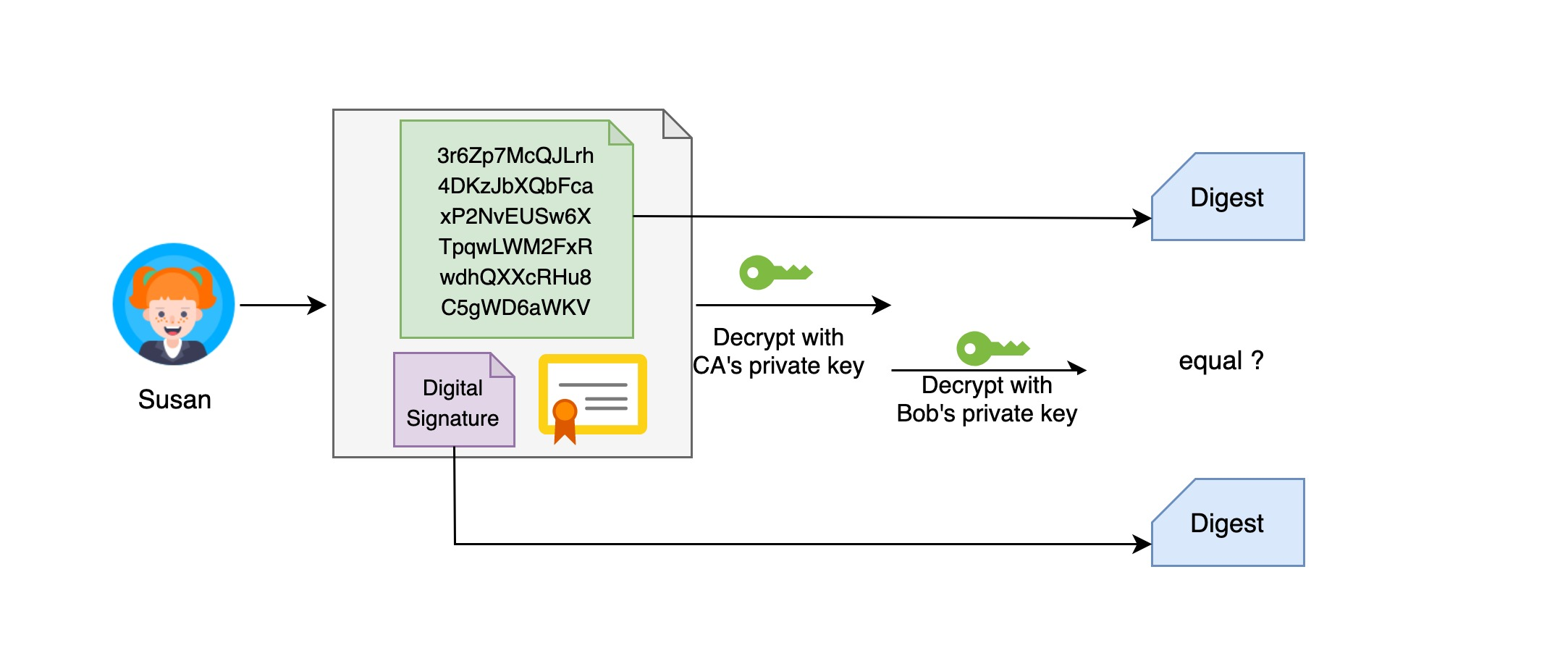
After Susan receives the letter, she first uses the CA’s public key (which is generally public) to decrypt the digital certificate, and then she can use this public key to decrypt the digital signature and further verify whether the contents of the letter have been tampered with.
Summary
In the communication process of asymmetric encryption, the private key is used to encrypt the original text, and then the ciphertext, the original text and the public key are published so that anyone can decrypt the ciphertext with the public key and then check whether the original text and the ciphertext are the same. The private key cannot be disclosed, which means that only the owner of the private key can encrypt the data using the private key, so this method can be used to prove that the person who published the message is indeed the person it claims to be, and at the same time, the use of digital signature can verify that the message has not been tampered with, which is the basic principle of this is the digital signature.
With a digital signature, then we can prove that a person has a private key corresponding to a specific public key through a digital signature, so the public key can be regarded as a digital identity mark. The digital certificate is generated by encrypting the basic information of the certificate owner, the information of the certificate issuer and the information of the certificate itself (expiration time, encryption algorithm, etc.) through the certificate center.
It can be seen that “digital certificate” is the solution to the problem of identity authentication, just as in reality each of us has to have an ID card or driver’s license to prove our personal identity, to indicate our identity or certain qualifications. The digital certificate is issued by an authoritative and impartial third-party organization, i.e., the certificate center, to ensure the confidentiality and anti-repudiation of information. For a large application environment, the certification center often adopts a multi-level hierarchical structure, and the certification centers at all levels are similar to administrative authorities at all levels, with the higher-level certification center responsible for issuing and managing the certificates of the lower-level certification center, and the lowest-level certification center directly facing the end users.