Ambient is a new data-plane model that Istio has just announced support for. In this post, we will try to install Istio’s ambient model and use the bookinfo demo to experience the L4 and L7 capabilities offered by ambient.
Note: L4 refers to the four layers of the OSI standard network model, i.e., TCP layer processing. L7 refers to layer seven of the OSI standard network model, which is the application layer processing, generally referred to as HTTP protocol processing.
Install Istio ambient mode
According to the ambient schema README documentation, ambient currently supports Google GKE, AWS EKS and kind k8s deployment environments . After my experimentation, kind on Ubuntu is the most convenient deployment environment to build. You can refer to Get Started with Istio Ambient Mesh to build a trial version of Istio with ambient support. If you do not have access to the official download address, you can download and install from the mirror I built in China by following these steps:
-
First install docker and kind on an Ubuntu virtual machine.
-
Create a kind k8s cluster
-
Then download and unzip the trial version of Istio that supports ambient mode.
-
install Istio, you need to specify the profile as ambient, note that you need to specify the hub, otherwise the relevant container image may fail to pull due to network reasons.
The ambient profile installs Istiod, ingress gateway, ztunnel and istio-cni components in the cluster. The ztunnel and istio-cni are deployed on each node as daemonset. istio-cni is used to detect which application pods are in ambient mode and create iptables rules to redirect outbound and inbound traffic from these pods to the node’s ztunnel. istio-cni will continuously monitors changes to the pods on the node and updates the redirection logic accordingly.
1 2 3 4 5 6 7 8 9 10$ kubectl -n istio-system get pod NAME READY STATUS RESTARTS AGE istio-cni-node-27f9k 1/1 Running 0 85m istio-cni-node-nxcnf 1/1 Running 0 85m istio-cni-node-x2kjz 1/1 Running 0 85m istio-ingressgateway-5c87575d87-5chhx 1/1 Running 0 85m istiod-bdddf595b-tn9px 1/1 Running 0 87m ztunnel-5nnnl 1/1 Running 0 87m ztunnel-dk42c 1/1 Running 0 87m ztunnel-ff26n 1/1 Running 0 87m
Deploy the demo application
Execute the following command to deploy the Demo application.
The above command deploys the Demo application in the default namespace. Since the default namespace is not tagged with the relevant label, the traffic of the Demo application does not go through ztunnel at this time, and the traffic between pods goes through the service mechanism for communication, and the traffic between pods is not authenticated and encrypted by mTLS.
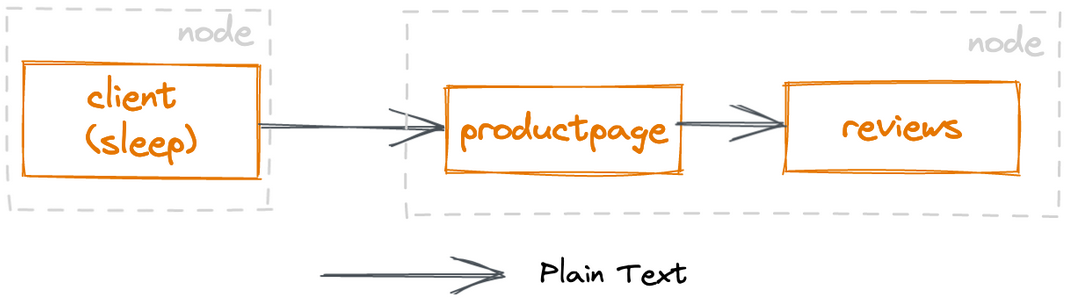
Communication between applications that are not included in ambient mode.
Include Demo applications in ambient mode
You can add all applications in a namespace to the ambient mesh by tagging the namespace with the following.
|
|
The istio-cni component will monitor that the namespace is added to the ambient mesh and will set the appropriate traffic redirection policy. If we check the istio-cni logs, we can see that istio-cni creates the appropriate routing rules for the application pod.
|
|
Access the productpage from sleep.
|
|
We should be able to see the output of the productpage service. At this point the traffic has been authenticated and encrypted in both directions with mTLS via ztunnel. We should be able to see the access logs from the ztunnel on the sleep and productpage nodes.
Traffic in the outbound direction (sleep -> ztunnel on the sleep node).
|
|
Traffic logs in the inbound direction (ztunnel -> productpage on productpage).
|
|
We can see that the outbound traffic log has the word (no waypoint proxy) in it because ambient’s current implementation only does L4 processing by default, not L7 processing. This is because ambient’s current implementation only does L4 processing by default, not L7, so the traffic will only go through the ztunnel and not the waypoint proxy, as shown in the figure below.
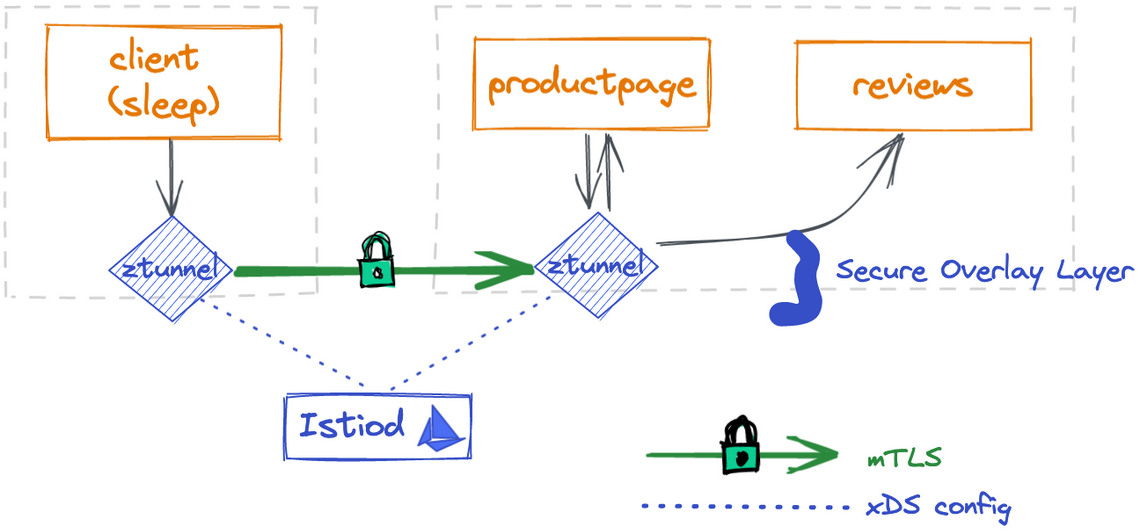
Applications communicate with each other through the ztunnel security overlay.
Enable L7 functionality for ambient mode
Currently ambient mode requires a gateway to be defined to show that seven layers of processing are enabled for a service. Create the following gateway to enable seven layers of processing for the productpage service.
Note that the gatewayClassName in the gateway resource created above must be set to ‘istio-mesh’ for Istio to create the corresponding waypoint proxy for the productpage.
You can see the waypoint proxy created by Istio at this point.
Access the productpage from sleep.
|
|
Let’s look at the actual path that the request goes through.
sleep -> ztunnel on sleep node.
|
|
You can see the words (to server waypoint proxy) in the log above, indicating that the request went through the waypoint proxy.
ztunnel on sleepnode-> waypoint proxy.
|
|
ztunnel on productpage node -> productpage.
|
|
When the L7 feature is enabled in ambient mode, the traffic path between applications is shown in the figure below.
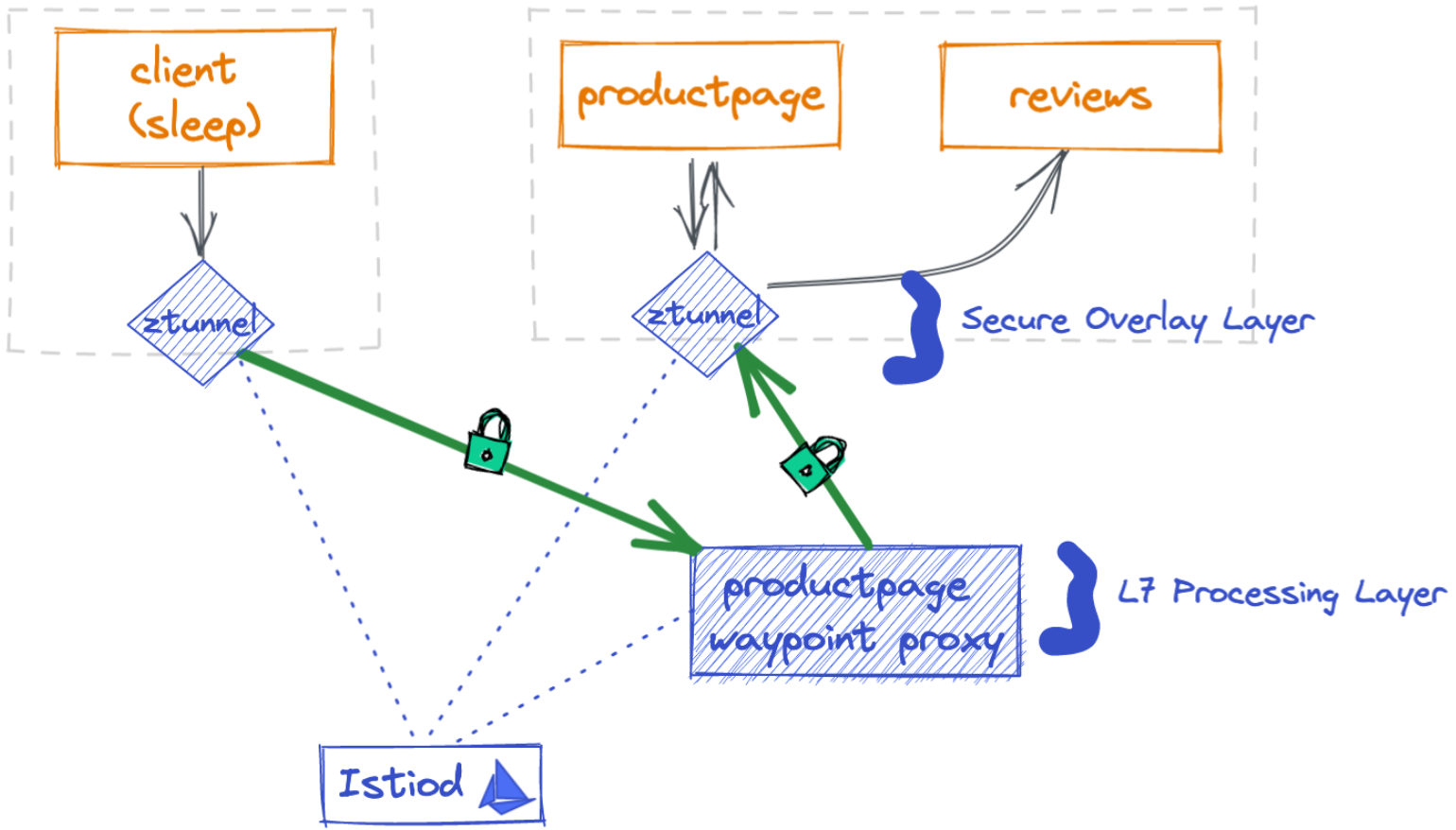
Application traffic path after enabling waypoint L7 processing
Routing traffic through all seven layers
Now let’s try to route the traffic at seven levels in ambient mode. ambient mode has the same routing rules as sidecar mode and also uses Virtual service.
First enable the L7 capability for the review service by creating a gateway.
Create VS and send requests to V1 and V2 versions in 90/10 ratio.
|
|
Execute the following command to verify that the reviews service requests are routed according to the routing rules defined above.
|
|
ambient pattern summary
From the above experiments, we can see that ambient mode has solved the deployment dependency problem of application and sidecar in Istio sidecar mode. In ambient mode, the capabilities of the service mesh are provided through ztunnel and waypoint proxy outside the application pod, and sidecar injection to the application pod is no longer required. As a result, the deployment and upgrade of application and mesh components are no longer dependent on each other, bringing the service grid down to the infrastructure level and fulfilling the promise that the service grid is the infrastructure that provides communication for applications.
Currently, to enable the L7 mesh capability for a service, you have to create a gateway, which is an additional burden for operations and maintenance. For the waypoint proxy issue that I was previously concerned about, which caused an increase in the scope of failures and unchanged fault location, the issue can also be better addressed as Istio creates a waypoint proxy deployment for each service account, as long as best practices are followed to create a different service account for each service. This problem can be solved by following best practices and creating different service accounts for each service. In addition, ambient is still in a rapid development iteration process, so I believe these minor issues will be resolved in subsequent releases soon.
Reference
https://istio.io/latest/blog/2022/get-started-ambient/https://www.zhaohuabing.com/post/2022-09-10-try-istio-ambient/