GitHub has released a blog post stating that it is taking steps to improve the security of its hosted code repositories. It will now be necessary to use the encrypted Git protocol when pushing and pulling Git data. These changes will affect some of the keys supported in SSH, and according to the Git Systems team, unencrypted Git protocols will now be a thing of the past.

Specifically, GitHub no longer supports DSA keys (Digital Signature Algorithm), and some traditional SSH algorithms such as HMAC-SHA-1 and CBC are no longer available. GitHub will add two new host keys for SSH – ECDSA and Ed25519, both of which are new standards based on elliptic curve encryption. There will also be a new requirement for RSA keys (Rivest-Shamir-Adleman), and additional security requirements will be met by SHA-2 signatures in the future.
The change does not affect all GitHub users
However, according to the systems team, most users will not be affected by this policy change. According to the announcement, only users who connect to the repository via SSH or git:// will be affected, and if your own Git starts with https://, you will also not be affected. GitHub also dropped password authentication for Git Actions a while back, and while there is no technical connection to the encryption requirements of the Git protocol, both of these changes are efforts by GitHub to keep user data safe.
Removing old key types
The GitHub team said that the reason for dropping the old key types and some of the algorithms used for signing is that more and more attacks and new methods of attack tend to cause more security problems with the original technology. What was considered secure decades ago is no longer necessarily applicable today; DSA keys are only 80-bit secure, while the standard is now 128-bit. While GitHub users should be more or less aware of this, according to internal GitHub statistics, 0.3% of GitHub requests are still using DSA.
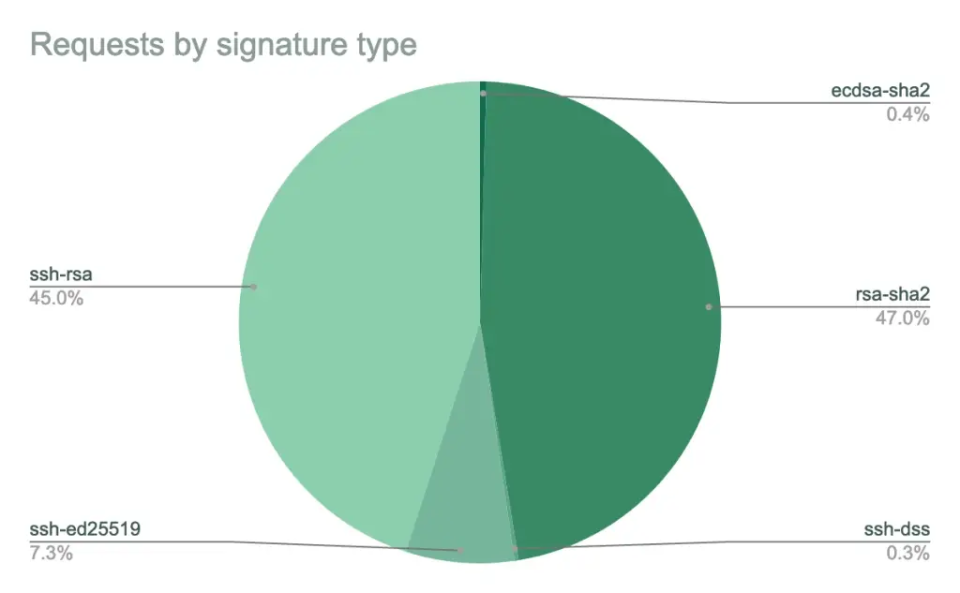
Remove insecure signature algorithms
A number of SSH clients today, including OpenSSH 7.2 (rsa-sha2-256 and rsa-sha2-512) and newer, have support for SHA-2 in combination with RSA. While RSA keys are considered more secure (ssh-rsa), they are often used in conjunction with outdated signature algorithms (based on SHA-1) in older Git clients. GitHub is now forcing new RSA clients to use SHA-2 signatures because of the vulnerability of the SHA-1 signature algorithm. Nevertheless, users can continue to use SHA-1 signatures for now, but as of November 2, 2021 all keys will need to be signed with SHA-2.
When will these changes take effect?
The Git team has shared a timeline of upcoming changes to the new host keys, ECDSA and Ed25519, which will be available via UpdateHostKeys-Extension as early as September 14, 2021. starting November 2, the option to set RSA keys using the SHA-1 algorithm will no longer be available, and SHA-2 will be mandatory at that time. Two new host keys, ECDSA and Ed25519, will be fully operational starting November 16, while the previous DSA host key will be withdrawn from support.