CentOS 7.0 has replaced the original firewall iptables with FirewallD, which supports IPv4, IPv6 firewall settings and Ethernet bridging, and has both runtime and permanent configuration options, and is called a dynamically managed firewall, meaning that changes can be applied without restarting the entire firewall. firewalld is installed by default, if not, execute yum install firewalld firewalld-config to install it, where firewalld-config is a GUI tool.
netfilter
iptables, firewalld, and other software do not have firewall functions, but they manage and maintain rules in user space, but the rules structure and usage are different. engine introduced in the Linux 2.4 kernel. It consists of packet filtering tables that contain the set of rules used by the kernel to control packet filtering. iptables, firewalld, etc. are all convenient tools for modifying filtering table rules in user space.
Linux internal structure can be divided into three parts, from the bottom to the top: hardware->kernel space->user space
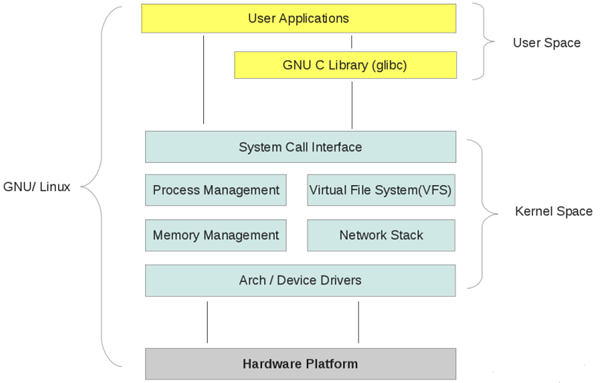
netfilter has a total of 5 control gates at locations where packets must pass through and rules can be read. The inspection rules at these five gateways are placed in five rule chains.
- PREROUTING packets just after they enter the network interface and before they are routed
- INPUT packets flowing from the kernel into user space
- FORWARD entering from one network interface and going to another in kernel space Forwarding filtering
- OUTPUT packets flow out of user space to kernel space
- POSTROUTING after routing, before the packet leaves the network interface
Chains are actually checklists containing numerous rules, and each chain contains many rules. When a packet arrives at a chain, the system starts checking from the first rule in the chain to see if the packet satisfies the conditions defined by the rule. If it does, the system processes the packet according to the method defined by the rule; otherwise, it continues to check the next rule, and if the packet does not meet any of the rules in the chain, the system processes the packet according to the chain’s pre-defined default policy.
When a packet enters the NIC, it first enters the PREROUTING chain, and the kernel determines whether it needs to be forwarded out based on the packet’s destination IP. If the packet is the one coming into the machine, it moves down the graph to the INPUT chain. Once the packet arrives at the INPUT chain, any process will receive it. Programs running on this machine can send packets that go through the OUTPUT chain and then arrive at the POSTROUTING chain output. If the packet is to be forwarded out and the kernel allows it, the packet will move to the right as shown in the figure, go through the FORWARD chain, and then reach the POSTROUTING chain output

As you can see, the packets just entering from the network interface have not yet made routing decisions and do not yet know where the data is going, so there is no way to implement data filtering at the import and export, so you need to set forwarding gates, entering user space gates and leaving user space gates in kernel space.
iptables
iptablses slices each of the five chains into five different tables according to purpose and usage. This means that each table can be configured with separate rules for certain chains as needed. For example, the mangle table and the filter table can both be configured with rules for INPUT chains, and when packets flow through the INPUT location (into userspace), the rules for the INPUT chains in both tables are used to do filter checks.
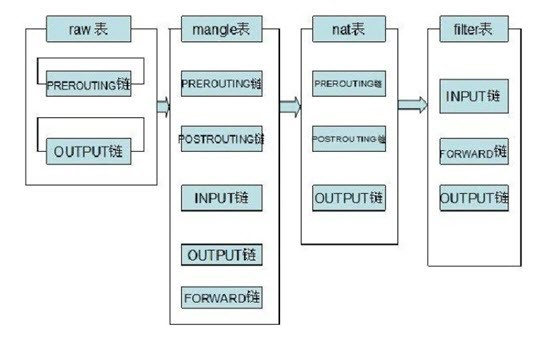
Five tables, each focusing on a different function
- filter Packet filter function. Only the INPUT, FORWARD, and OUTPUT chains are involved. It is the default table manipulated by the iptables command.
- nat address translation function. nat translation involves only three chains PREROUTING, OUTPUT, POSTOUTING. It can be forwarded to allow LAN machines to connect to the Internet
- mangle packet modification function. Modification operations can be done on each chain. Modify packet metadata, firewall tagging, etc.
- raw fast channel function. For efficiency, highest priority, packets that match the raw table rules will skip some checks.
- security Needs to be used in conjunction with selinux. The built-in rules are more complex and are usually turned off.
iptables also supports custom rule chains. The custom chain must be associated with a particular chain. Rules can be set in a chain, and packets that meet certain conditions jump to a certain target chain for processing, and then return to the current chain to continue processing subsequent rules after the target chain has finished processing. Because the rules in the chain are checked sequentially from the beginning to the end, the order of the rules is very important. The stricter the rule should be the more forward.
iptablse service management
|
|
iptables Command Reference
|
|
The default table name is FILTER. the serial numbers (RULENUM) used in the command are based on 1.
COMMAND command options
|
|
CRETIRIA Conditional Matching
There are basic matching and extended matching, and extended matching is divided into implicit matching and display matching.
Basic match: (you can use ! can negate a subclause, such as -p !tcp)
|
|
Extended match: (e.g.: -p tcp -m tcp -dport 80)
|
|
Implicit Extended Matching
An extension to -p PROTO, or an additional match condition to -p PROTO, -m PROTO can be omitted, hence the name implicit
|
|
Show extended matches
|
|
ACTION Target Strategy (TARGET)
|
|
Auxiliary options.
|
|
state TCP link status
Examples of use:
|
|
FirewallD
FirewallD is related to iptables.
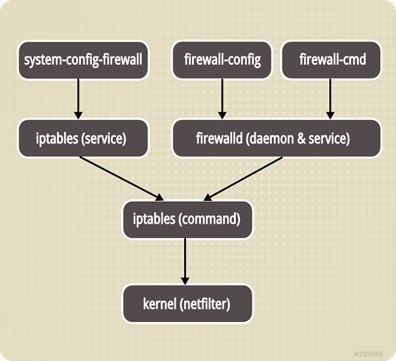
The underlying firewalld is still based on iptables, but there are still many differences.
- iptables stores configuration in /etc/sysconfig/iptables, while firewalld stores configuration in various XML files in /usr/lib/firewalld/ and /etc/firewalld/, where the former is the default configuration, please do not modify it. You can edit your own configuration in /etc/firewalld/, and firewalld takes precedence over the configuration in /etc/firewalld/.
- With iptables, each individual change means clearing all old rules and reading all new rules from /etc/sysconfig/iptables, yet with firewalld no new rules are created; only the differences in the rules are run. Thus, firewalld can change settings during runtime without losing existing connections.
zone concept in firewalld
RHEL7, however, seems to be implemented in the same way as iptables, but unlike mariaDB, which is compatible with MySQL commands, FirewallD cannot resolve firewall rules added by the ip*tables and ebtables command line tools
FirewallD is managed using the concept of zones, one for each NIC, and the configuration files for these zones can be found under /usr/lib/firewalld/zones/, with the default being public.
- drop Any packets flowing into the network are dropped without any response. Only outgoing network connections are allowed.
- block (blocking) Any incoming network connection is rejected and returns an icmp-host-prohibited message for IPv4 or an icmp6-adm-prohibited message for IPv6. Only network connections initialized by this system are allowed.
- public In the section that is used to be public. You believe that other computers on the network are untrustworthy and could harm your computer. Allow only selected connections to access.
- external is used to enable disguised external networks such as routers. You believe that other computers on the network are untrustworthy and could harm your computer. Allow only selected connections to access.
- dmz (quarantine zone) is used to allow computers in the quarantine zone (dmz) to have limited access to the outside network. Only selected connections are accepted.
- work is used for working networks. You trust that most of the computers on the network will not affect your computer. Accept only selected connections.
- home is used on home networks. You trust that most of the computers in your network will not affect your computer. Only selected connections are accepted.
- internal is used on internal networks. You trust that most of the computers in the network will not affect your computer. Only selected connections are accepted.
- trusted allows all network connections.
Filtering rules in firewalld
- source: Filter by source address
- interface: Filter by NIC
- service: filter by service name
- port: filter by port
- icmp-block: icmp message filtering, configured by icmp type
- masquerade: ip address masquerade
- forward-port: port forwarding
- rule: custom rule
The priority of the filtering rules follows the following order
- source
- interface
- conf
firewalld common commands
fierwalld can be configured directly by modifying the configuration file, or through the commands of the configuration tool.
First check the value of DefaultZone in /etc/firewalld/firewalld.conf, the default is DefaultZone=public, at this time /etc/firewalld/zones/ directory should have a public.xml file, vi open it to modify to.
|
|
This means opening ssh (22), http (80), https (443) ports in the public zone, which corresponds to each of the service types defined in the *.xml file under /usr/lib/firewalld/services/, for example, the http.xml file is as follows.
|
|
So it can also be done directly in public.xml like this.
|
|
Each time you change the configuration file or more trouble, firewalld can use firewall-config and firewall-cmd for configuration, the former is due to the GUI mode, the latter for the command line tools, some common commands are as follows.
|
|
Some common parameters of the commands are described as follows
- -zone=ZONE Specify the zone where the command works, if it is missing, the command works on the default zone.
- -permanent with this parameter means that the command only modifies the configuration file and requires reload to take effect; without this parameter, it takes effect immediately in the current running instance, but it will not change the configuration file, and restarting firewalld service will have no effect.
- -timeout=seconds indicates the duration of the command effect, which will be removed automatically after expiration, and cannot be used with -permanent at the same time. For example, if a configuration is added for debugging purposes, it will be removed automatically when the time is up, so you don’t need to come back and remove it manually. You can also add a specific rule when an exception occurs and automatically remove it after a period of time.