The network layer protocol assumes the two major functions of packet forwarding and routing, and it can provide the upper layer with the responsibility of transporting packets between different hosts. IP protocol, as a network layer protocol, plays an extremely critical role in today’s Internet, although it can only provide connectionless and unreliable services.
In general, when we want to access services provided by other hosts, we need to access the target host through an IP address, which is the only way to be accessed by other hosts on the Internet. IP addresses are like home addresses, and we need to ensure that all host IP addresses are unique so that we can find the correct host.
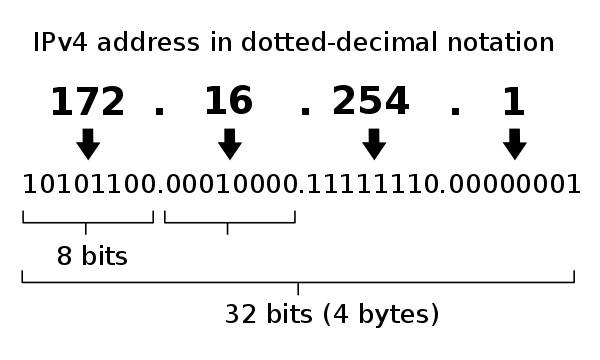
The first major version of the IP protocol, IPv4, which was created in 1974, uses a 32-bit representation of addresses and provides a total of 2^32 (4,294,967,296) IP addresses. 4.2 billion IP addresses may seem like a lot, but the number of available IPv4 addresses has been decreasing in recent years, and as early as 2011, the top IPv4 addresses were were all allocated
To address the imminent exhaustion of IP addresses, the IETF released a draft of the IPv6 protocol in 1998 and it officially became an Internet standard in 2017. IPv6 uses 128-bit IP addresses, which can represent a total of 2^128 addresses, and IPv6 can even assign separate addresses to the sands of the earth:
2128=340282366920938463463374607431768211456≈3.4∗1038
The designers of the IPv6 protocol originally thought that IPv6 would be adopted rapidly as IPv4 addresses dwindled, and they originally estimated that IPv6 would be deployed worldwide by 2003, but from today’s perspective, these predictions were overly optimistic. These predictions are still overly optimistic from today’s perspective.
The question we want to analyze in this paper is why, with all its benefits and ability to solve the IPv4 address shortage, the IPv6 protocol has not been adopted on a large scale even 17 years after the original prediction of 2003. We will discuss several reasons for this here.
- NAT technology has largely alleviated the IPv4 address shortage.
- IPv6 protocols were not designed with compatibility with IPv4 in mind.
- finer-grained control of IPv4 addresses and recovery of idle resources.
NAT
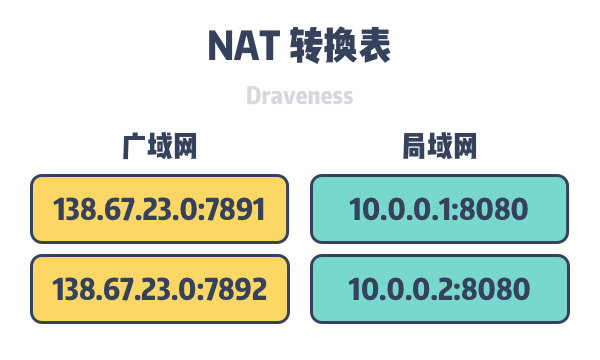
Network Address Translation (NAT) is a technology that modifies network addresses as IP packets pass through a router, mapping the IP address in the current address space to another address space. When switching networks or upstream ISPs change, NAT technology can avoid modifying the IPs of all nodes in the network. We can think of NAT technology as a translation table that stores the translation relationships from external addresses and ports to internal addresses and ports.
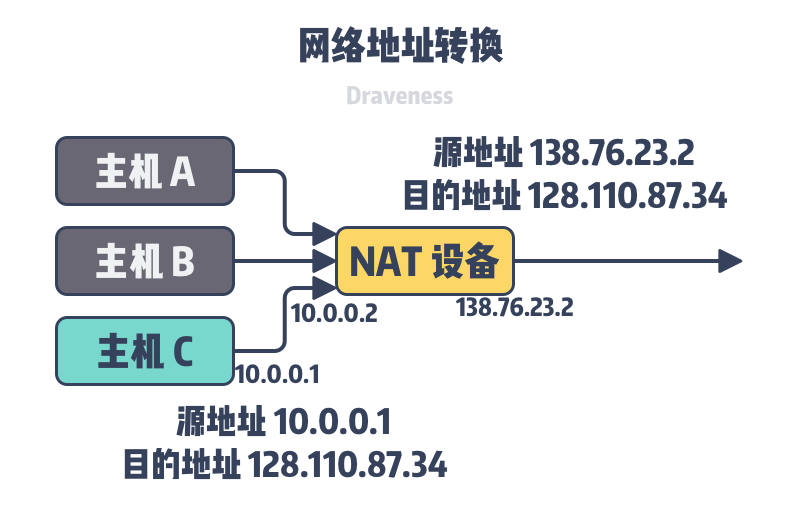
When a packet accesses the external network from the inside, the NAT assigns a port to the current request, overwrites the source address and port in the packet, and stores the address and port information in a local translation table; when a packet enters the internal network from the outside, the NAT looks up the IP address and port number of the packet to the corresponding host and port number in the private network and overwrites the destination address and port in the packet.
With NAT as an intermediate layer, we can not only protect our private network, but also alleviate the shortage of IP addresses. However, NAT technology does not have only benefits, it also brings a lot of problems. In addition to the fact that a host under a NAT network does not have a true end-to-end connection to the other side and cannot participate in some of the Internet protocols, the NAT protocol brings the following problems that are controversial.
- the port numbers used by NAT are for process addressing and not for host addressing.
- that the NAT router, as a Layer 3 (network layer) device, should only handle packets that reach the network layer
- that NAT violates the principle that hosts should talk directly to each other.
Although NAT brings a lot of controversy and problems, NAT has become a widely used technology throughout the Internet, and engineers have tried to solve the problems it brings through various NAT traversal techniques, such as SOCKS, UPnP and ALG, etc.
Compatibility
Software and protocols are designed for the present and the predictable future, but it is difficult to predict the specific future trend, and the current design will gradually become inapplicable as the scenario changes. All software and protocols need to be updated and iterated, and in the process of updating we need to consider compatibility, which can generally be divided into Forward compatibility and Backward compatibility.
- Forward compatibility: the old version of the system can receive and process the data generated by the new version of the system.
- Backward compatibility: the new version of the system can receive and process the data generated by the old version of the system.
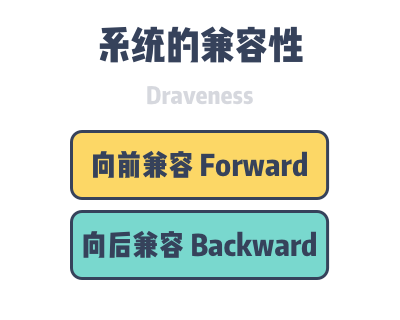
If the IPv6 protocol is forward-compatible with IPv4, then the hardware devices used to handle IPv4 can handle IPv6 data without updating, but the benefits of IPv6 cannot be enjoyed without updating the system; if the IPv6 protocol is backward-compatible with IPv4, then the IPv6 hardware can If the IPv6 protocol is backward-compatible with IPv4, then IPv6 hardware can handle both IPv4 and IPv6 packets, and the entire network can be upgraded seamlessly by replacing IPv4 devices with IPv6 devices.
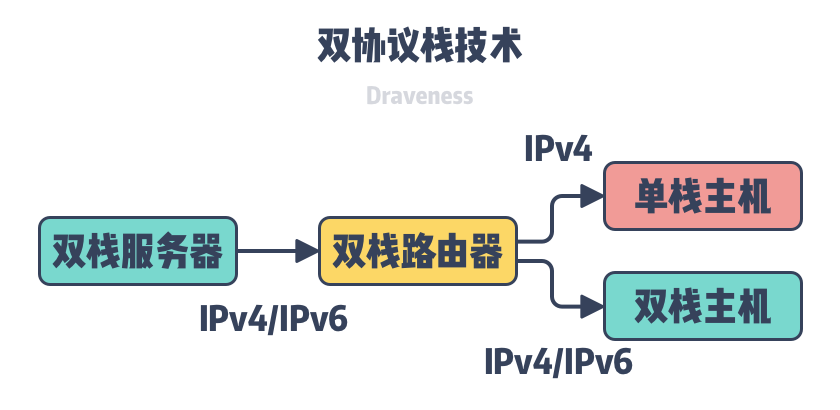
If IPv4 and IPv6 were forward-compatible or backward-compatible, the advancement of the IPv6 protocol might not be so complicated, but the IPv6 protocol was not designed with compatibility with earlier versions of the protocol in mind. Although IPv4 and IPv6 are both IP protocols, they are not compatible with each other, so we can only transition protocols through dual stacks, tunneling, or NAT64.
It is understandable that the IPv6 protocol wants to get rid of the historical baggage and achieve a completely incompatible design. In the process of applying the IP protocol in the past decades, we have encountered many problems, and it is not impossible to move forward with the historical baggage, but as the core protocol of the Internet, although the designers of the IP protocol admit that the failure of IPv6 to achieve backward compatibility is the biggest mistake, the authors believe that it is good in the long run to get rid of the historical baggage quickly through incompatibility.
Address Control
IPv4 addresses are indeed a scarce resource in general, but like other scarce resources, it has always been a major issue to allocate them properly and provide utilization. ) are the organizations responsible for assigning IP addresses. Except for some IP addresses reserved for proprietary networks, the remaining addresses are generally assigned in the form of address blocks through subnets.
In the early development of the Internet Protocol, subnets were divided by the leftmost 8 bits of the IP address, but because this allowed only 256 networks to be divided, it was quickly replaced by the Classful Network Architecture in 1981. The Classful Network Architecture contains three types of networks, A, B and C
| Class | Number of Networks | Number of Hosts |
|---|---|---|
| A | 128 | 16,777,214 |
| B | 16,384 | 65,534 |
| C | 2,097,152 | 254 |
Class A addresses can only be assigned to 128 different networks, each of which can contain 16 million hosts, while Class C addresses can be assigned to 2 million organizations and the network can contain more than 200 hosts. By classifying IP addresses, we are able to assign IP address blocks more rationally, but although it classifies IP addresses, it is still a crude division of addresses.
The IETF proposed Classless Inter-Domain Routing (CIDR) in 1993 as an alternative to the classified network architecture, which is based on Variable-length Subnet Masking (VLSM) and has two main purposes
- mitigating the rate of growth of router transit tables in the Internet.
- mitigating the rate of IPv4 address exhaustion.
The segmentation of addresses in the classified network architecture is still a bit too ideal, as too small address blocks are often insufficient and slightly larger address blocks are more wasteful. Unlike categorical network architectures that use only fixed-length subnet masks of 8, 16, and 24 to divide IP address blocks into three classes, CIDR uses variable-length subnet masks to divide address blocks, as shown in the CIDR representation below, where N denotes the prefix length, which can be any value from 0 to 32.
|
|
A.B.C.D/8, A.B.C.D/16, and A.B.C.D/24 can represent different address blocks of A, B, and C, respectively, in a categorical network architecture, while other numbers can be used to more flexibly represent a specific number of networks and hosts in a subnet.
In addition to more granular address allocation, recycling and reusing IP resources that are no longer in use is an important means of extending the life of IPv4, but we won’t go into that here. From IP address allocation, we can see the change of attitude towards resource usage from abundant to scarce, from the first rough allocation to the later fine-grained control, abundant resources will always be abused, and only when resources become really scarce, we start to calculate carefully.
Summary
Nearly 40 years have passed since the IPv4 protocol was released in 1981, and in that time it has assumed significant responsibility for packet forwarding and routing as a key protocol in the Internet protocol cluster, and as network environments and end devices have become more complex, we have needed more IP addresses to meet today’s needs.
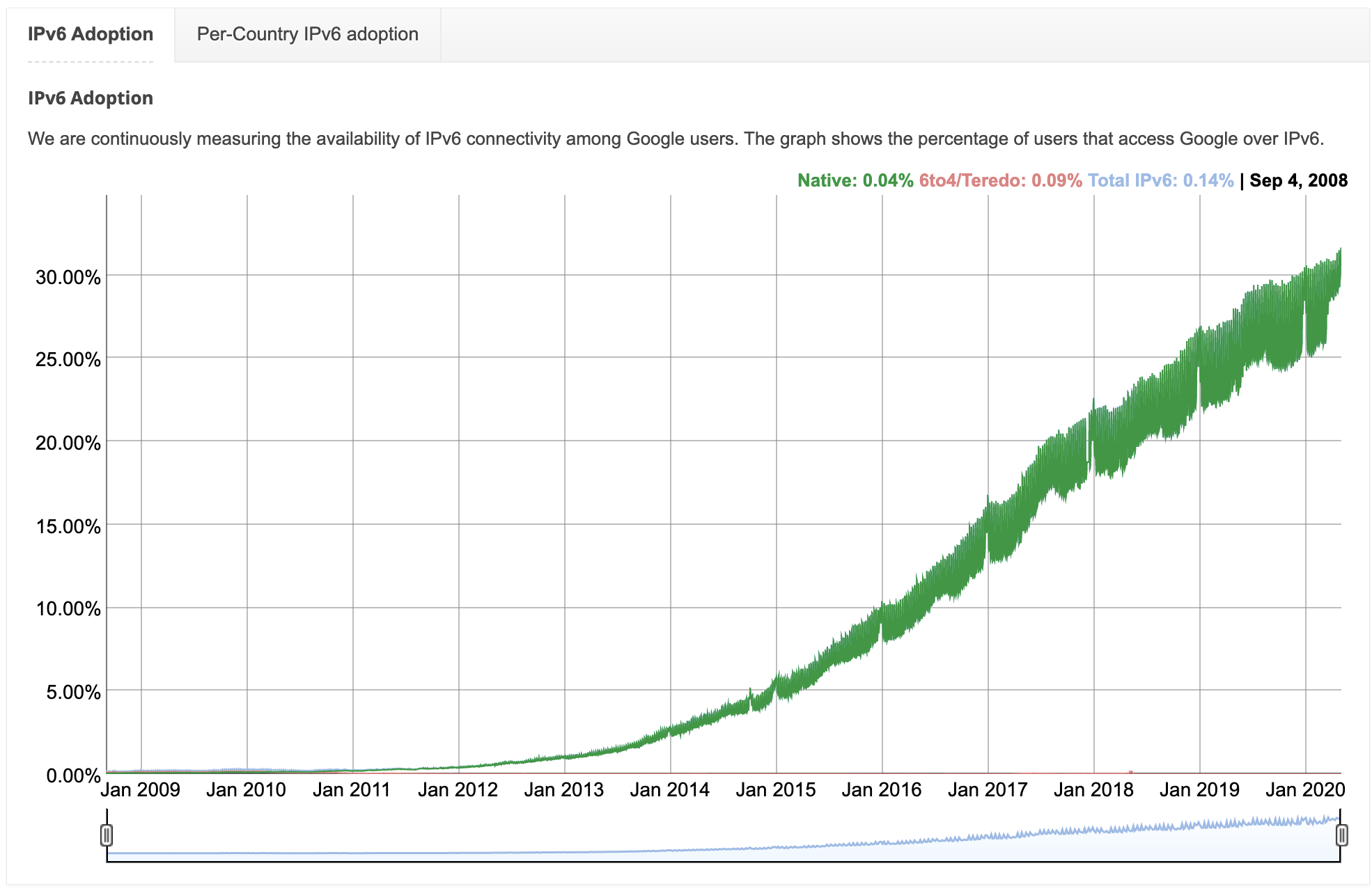
The IPv6 protocol has shed much of its historical baggage, and while more and more websites and network devices are beginning to support IPv6, it is difficult for IPv6 to completely replace IPv4 for many reasons, so let’s revisit the content of this article.
- NAT technology can largely alleviate the IPv4 address shortage and protect private internal networks, providing a firewall function.
- IPv4 and IPv6 protocols are completely incompatible, and we need to introduce dual stack, tunneling, or NAT64 to address compatibility issues, and there are additional costs associated with applying these technologies.
- IP address exhaustion can be delayed by fine-grained control of resources and reclaiming IP addresses that are no longer in use.
The imagination of engineers is boundless, and over the last decade or so we have tried to renew the IPv4 protocol in various ways to slow down the exhaustion of IP resources, but in the foreseeable future the IPv4 protocol will be replaced by IPv6 and we will have an almost endless supply of IP addresses. Finally, let’s look at some of the more open-ended questions that interested readers can ponder.
- What does the IPv5 protocol do? Why haven’t you heard of the IPv5 protocol?
- How soon do you think the IPv6 protocol will overtake IPv4 in terms of share?