cURL author Daniel Stenberg recently posted a tweet on Twitter, spilling the beans on a recent “funny thing” he encountered “. It started last Friday when Daniel Stenberg received an email from a Fortune 500 company (the screenshot obscures the company name, which will be replaced by XXXX below), in which the person said.
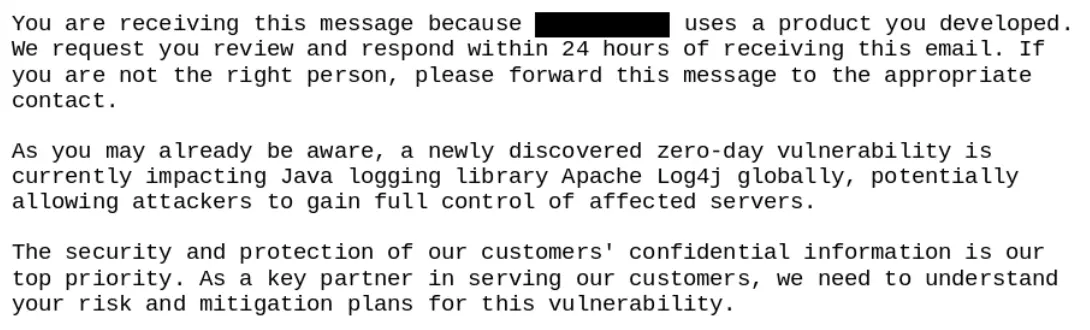
At the bottom of the email, the Fortune 500 company listed a series of questions for Daniel Stenberg to answer, including.
- Has your company had any confirmed security incidents?
- If so, which applications, products, services and related versions were affected?
- Have any XXXX products and services been affected?
- Has XXXX non-public information or personal information been affected?
- If so, please provide details of the affected information to XXXX immediately.
- What is the timeline for completing remediation? List the steps and include the dates for each step.
- What action is required of XXXX to complete this remediation?
- ……
After receiving this email, Daniel Stenberg found it very puzzling, since Log4j was originally written by Ceki Gülcü and is now being developed and maintained by the Apache Software Foundation, and Daniel Stenberg has never been involved in any development of Log4j. Daniel Stenberg never had any involvement in the development of Log4j. Daniel Stenberg had “nothing to do with this”, so to speak.
So, Daniel Stenberg replied in an email.
I will be happy to answer all of the above questions once we have a support contract in place.
Of course, the reply was followed by a tweet on Twitter.
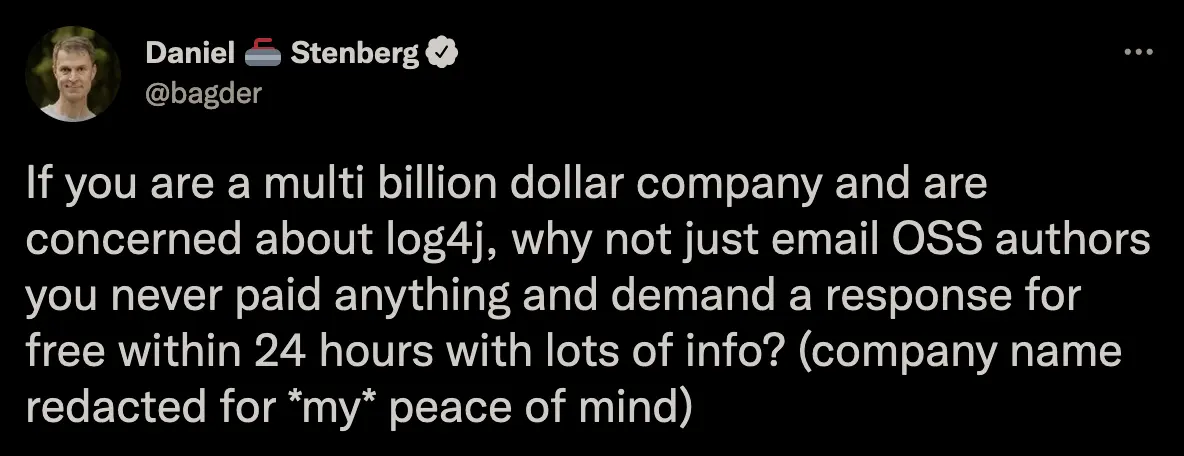
From this incident, we can see that there are indeed large enterprises do not care about the underlying project, or even understand how the underlying project works, these companies build their own business projects on top of the underlying project they do not care much, and make a very substantial profit from it.
Not only that, but the Log4j security breach has been festering for nearly two months, and many of the questions listed in the emails are publicly available information that corporate security departments can get answers to with a casual search engine.
So which Fortune 500 company is the one that is only now thinking about fixing the Log4j problem?