Communication flow
The communication to be described here is the process by which a user connects to the Onion service through the tor browser.
For ease of expression, Alice is used here to denote the client and Bob to denote the server.
Step 1: The server side sets up its own introductory node
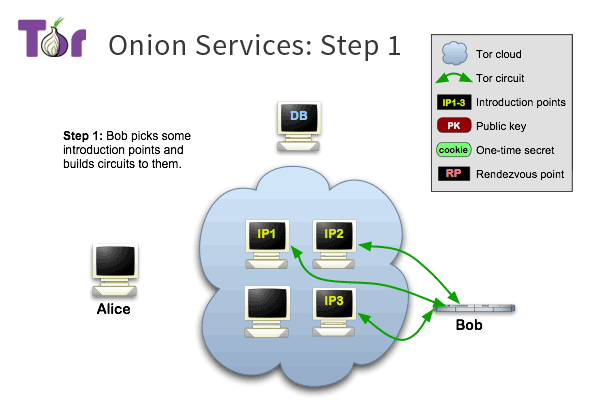
The server uses introduction points to forward the introduction messages from the client in order not to reveal its IP.
First, Bob selects a few nodes from the tor relay node list to be his introduction nodes, and then establishes long-term circuits with them.
The long connections here are established through the tor network, so they are anonymous and the introductory nodes do not know Bob’s IP.
At the same time, Bob will send an authentication key to the introductory node, and when a client connects to the introductory node, it will be able to determine whether the connection is to Bob by this key.
Step 2: The server side exposes its own information
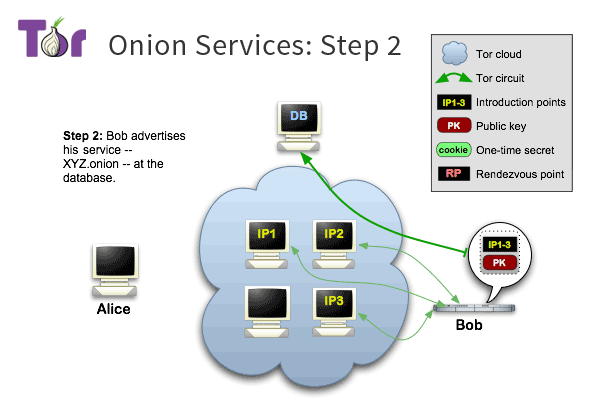
Bob generates a description message (onion service descriptor), which stores a list of introductory nodes, including the ip of the introductory node and the corresponding authentication key.
Bob then signs the message with his private key and publishes the message to Tor’s DHT.
After this step, the tor client can retrieve the message from the DHT with a certain key to find Bob’s introductory node.
Step 3: Client gets list of introductory nodes
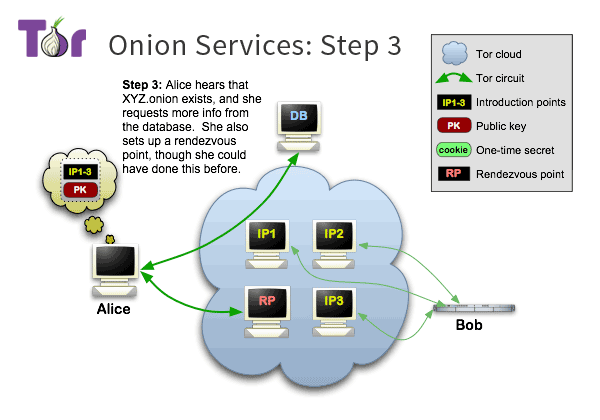
Alice (the client) knows from some sources that Bob has an onion service and knows the onion domain name of this service, e.g., xyz.onion, and Alice wants to access Bob.
First, she requests the information corresponding to that domain name from the DHT network, which is the description message posted by Bob in step 2.
After getting the message, Alice verifies its signature. The public key of Bob used for verification is actually encoded in the domain name xyz.onion, and Alice can decode it from the domain name.
The message is OK, Alice parses the list of Bob’s introduction nodes from the message, and selects one of the introduction nodes, where Alice will introduce herself to Bob.
Step 4: Client selects a rendezvous node
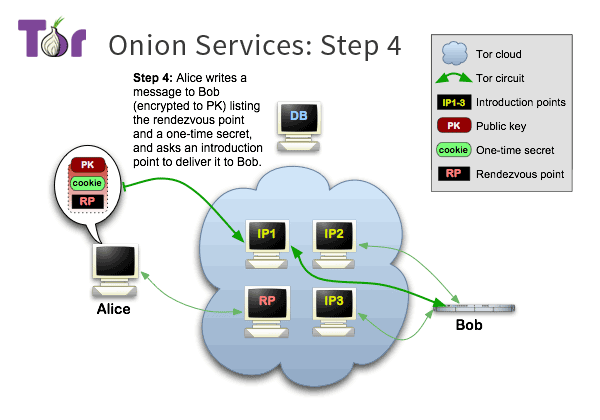
Alice selects a node from the tor relay node list as the rendezvous point, and then establishes a connection to the rendezvous node (RP) via tor.
At the same time, Alice sends a one-time secret to the rendezvous node, which will be used during the round.
Step 5: The client introduces itself to the server
Alice generates a message containing the rendezvous node and the one-time secret, and then encrypts the message with Bob’s public key.
Alice connects to one of Bob’s introduction nodes via the Tor network and has that introduction node forward the encrypted message to Bob.
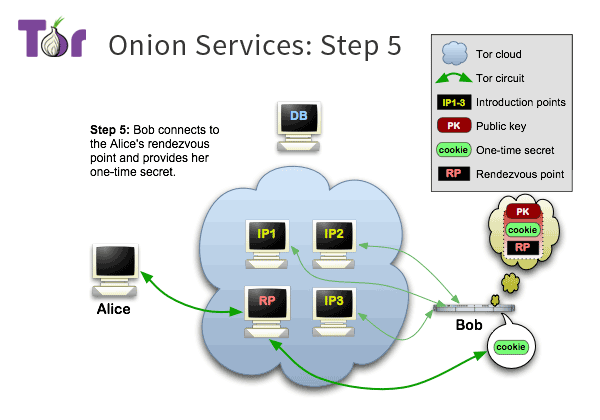
Step 6: Server-side and client-side rendezvous
At this point, Bob has received the message forwarded by the introduction node, knows that Alice wants to visit himself, and knows the information of the rendezvous node.
Bob connects to the rendezvous node through the Tor network, and then sends the one-time password received to the rendezvous node, from which the rendezvous node knows that Bob is trying to communicate with Alice, so that it can relay Alice’s messages to Bob.
Security
The client and the server end up communicating through the rendezvous node, and they each connect to the rendezvous node separately through the tor network, thus ensuring both the client’s invisibility and the server’s non-exposure.
All the communication in the above process is established using the tor network, including the communication between the server and the introduction node, the communication between the client and the introduction node, the communication between the client and the rendezvous node, and the communication between the server and the rendezvous node.
Therefore, normally the tor client communicates with the onion service after 6 transit times, including 3 times for the client to connect to the rendezvous node and 3 times for the server to connect to the rendezvous node.
If the tor client accesses a service other than the onion service, then the communication process is not the same as above, and there are only 3 transitions.