A veth virtual network device is connected to a protocol stack on one end and another veth device on the other end instead of a physical network. A packet sent out of a pair of veth devices goes directly to another veth device. Each veth device can be configured with an IP address and participate in the Layer 3 IP network routing process.
The following is an example of a typical veth device pair.
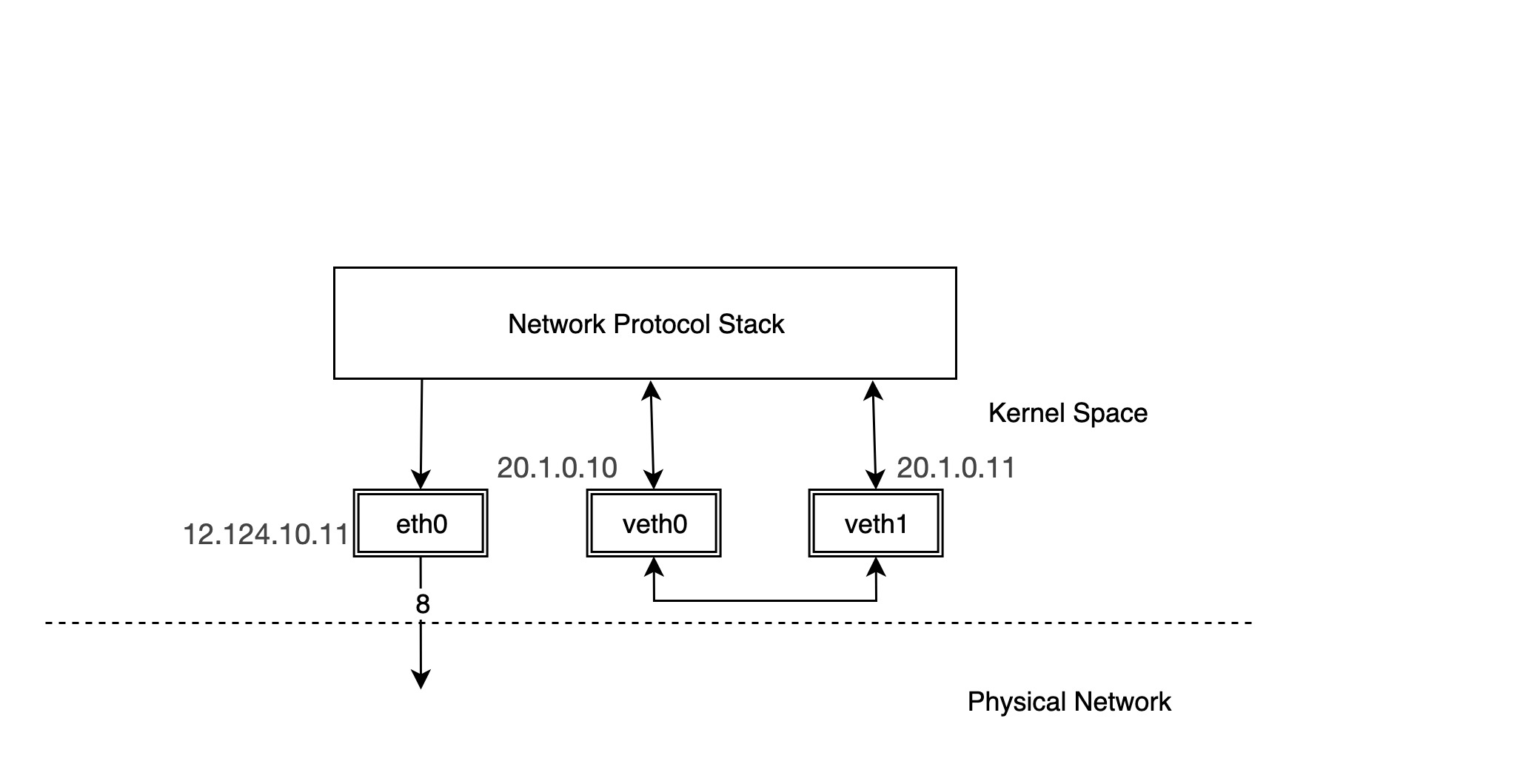
We configure the physical NIC eth0 with an IP of 12.124.10.11, and the veth devices that appear in pairs are veth0 and veth1 with IPs of 20.1.0.10 and 20.1.0.11, respectively.
Then try to ping the other device veth1 from veth0 device:
|
|
Note: In some Ubuntu devices, the ping may not work because the default kernel network configuration causes the veth device pair to fail to return ARP packets. The solution is.
You can try using tcpdump to see the request packets on the veth device pair.
|
|
You can see that there are only ICMP echo request packets on veth1, but no answer packets. If you think about it, veth1 receives the ICMP echo request packet and forwards it to the protocol stack at the other end, but the protocol stack checks the current device list and finds that there is 20.1.0.10 locally, so it constructs the ICMP echo reply packet and forwards it to the lo device, which receives the packet and hands it directly to the protocol stack and then gives it to the ping process in user space. After receiving the packet, the lo device directly hands it over to the protocol stack and then to the ping process in user space.
We can try to capture the data on the lo device using tcpdump.
|
|
It follows that for pairs of veth devices that appear in pairs, packets going out from one device are sent directly to the other device. In practical application scenarios, such as container networks, pairs of veth device pairs are in different network namespaces and packets are forwarded between between network namespaces, which will be explained in detail later when introducing container networks.
Reference https://houmin.cc/posts/680a2369/