Overview
SSL (Socket Layer Security) and TLS (Transport Layer Security) are both security protocols whose main purpose is to ensure secure communication between the client and the server; SSL is the older protocol and TLS is the replacement for SSL.
SSL versions 1.0, 2.0 and 3.0 and TLS versions 1.0, 1.2 and 1.3. SSL protocol and TLS 1.0 have been disabled due to obsolescence and TLS 1.3 is currently the most deployed security protocol on the Internet and it is the latest version of TLS which enhances the obsolete security and adds more touchability. The following points provide a brief overview.
- The advantages of the latest TLS 1.3
- What forward secrecy
- Why choose GCM encryption
TLS 1.3
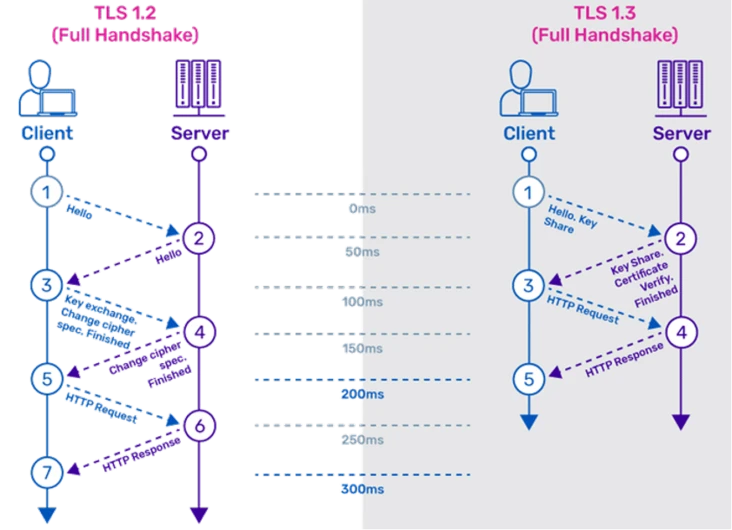
Modern browsers support both TLS 1.2 and TLS 1.3 protocols, but version 1.3 is much better. TLS 1.3 has several improvements over earlier versions, most notably a simplified TLS handshake, resulting in shorter handshake times, improved site performance, an improved user experience, and a more secure and simple cipher suite of support.
Cipher suites
TLS/SSL uses one or more cipher suites. A cipher suite is a combination of authentication, encryption, and message authentication algorithms. the algorithms used in TLS version 1.2 had a number of weaknesses and security vulnerabilities. These algorithms were removed in TLS 1.3.
- SHA-1
- RC4
- DES
- 3DES
- AES-CBC
- MD5
Another important update is that TLS1.3 supports the perfect-forward-secrecy (PFS) algorithm.
Forward Secrecy
Pass Forward Secrecy (PFS) is a feature of specific key negotiation protocols that allows hackers to intercept large amounts of data if a long-period session key is compromised, and we can generate a unique session key for each session, where the compromise of a single session key does not affect any data outside of that session.
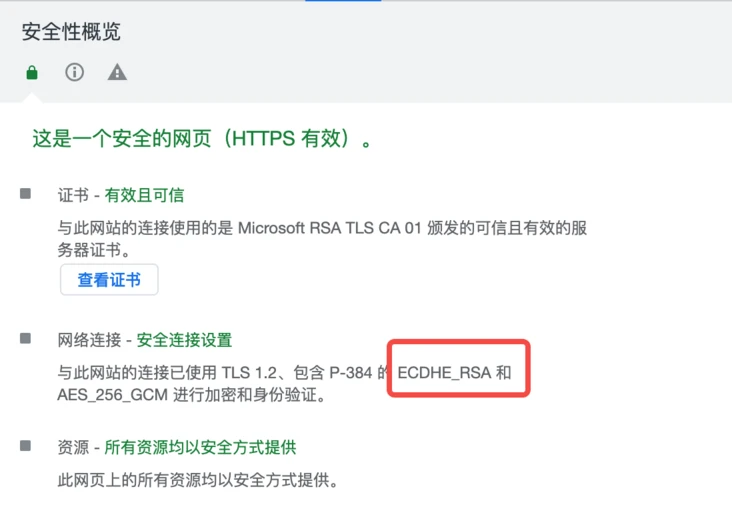
TLS in earlier versions could exchange keys during the handshake using one of two mechanisms: static RSA keys and Diffie-Hellman keys. In TLS 1.3, RSA and all static (non-PFS) key exchanges have been removed, leaving only DHE, ECDHE
- Temporary Diffie-Hellman (DHE)
- Provisional Elliptic Curve Diffie-Hellman (ECDHE)
You can check the security details of the site to confirm whether it uses “ECDHE” or “DHE”.
Why choose GCM
AES (Advanced Encryption Standard) symmetric encryption, which is the Advanced Encryption standard. The earlier encryption standard DES (Data Encryption Standard) has been deprecated.
AES choose the appropriate encryption mode is very important, the two more applied mode CBC and GCM.
CBC Cipher Group Linking Mode
The plaintext is chunked, the first block uses an initialization vector, and each subsequent plaintext block is anisotropic with the previous ciphertext block before encryption.
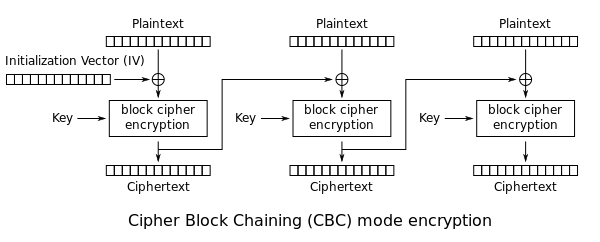
Problems with this model.
- If an error occurs in one plaintext block it will affect all subsequent blocks.
- No parallel processing, which limits throughput.
- Lack of built-in authentication, which is subject to some attacks, e.g., selective plaintext attack (CPA), selective ciphertext attack (CCA), etc.
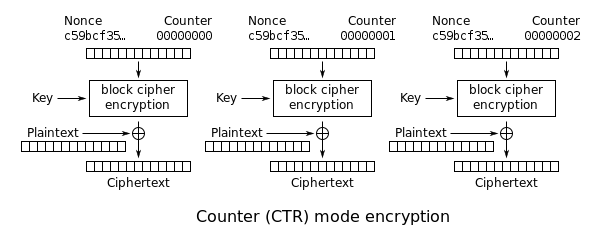
CTR Counting Mode
The plaintext chunks are numbered sequentially and the next block of the keystream is generated by encrypting successive values of the “counter” CTR mode is ideal for running on multi-core processors, where the plaintext chunks can be encrypted in parallel.
GCM Galois/Counter Mode
GCM = CTR + Authentication. its encryption process, the plaintext blocks are numbered sequentially, then this block number is combined with the initial vector and encrypted using block cipher E. The result of this encryption is then dissociated from the plaintext to generate the ciphertext.
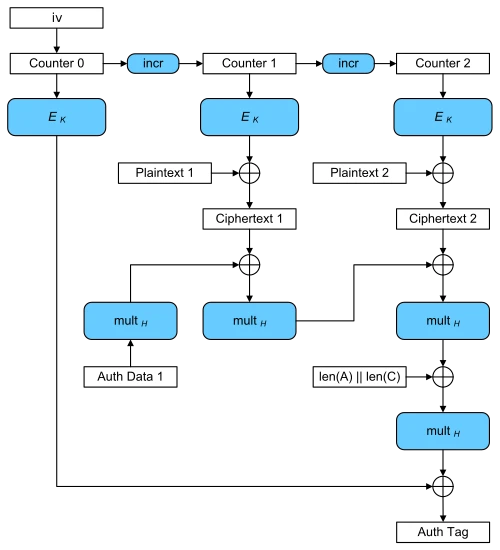
Simply put, GCM is a combination of CTR authentication, which is faster and more secure. It will accept pipelined and parallelized implementations and has minimal computational latency, so it is more widely used.
Nginx configuration
TLS1.2 support
Minimum client version:
- Supports Firefox 27+
- Android 4.4.2+
- Chrome 31+
- Edge, IE 11 on Windows 7 or above
- Java 8u31
- OpenSSL 1.0.1
- Opera 20+
- Safari 9+
|
|
TLS1.3 support
Minimum client version:
- Firefox 63+
- Android 10.0+
- Chrome 70+
- Edge 75
- Java 11
- OpenSSL1.1.1
- Opera 57
- Safari 12.1
|
|
It is generally recommended to be compatible with both 1.2 and 1.3.
|
|
Testing
Test for TLS 1.2 support.
|
|
Test for TLS 1.3 support.
|
|