Technology giant Microsoft recently announced that it will open source Cloud Katana, a cloud-native serverless application built on top of Azure Functions that can be used to perform security assessments of cloud and hybrid cloud environments. While it is currently only available for Azure, Microsoft developers are working to make it compatible with other cloud service providers.
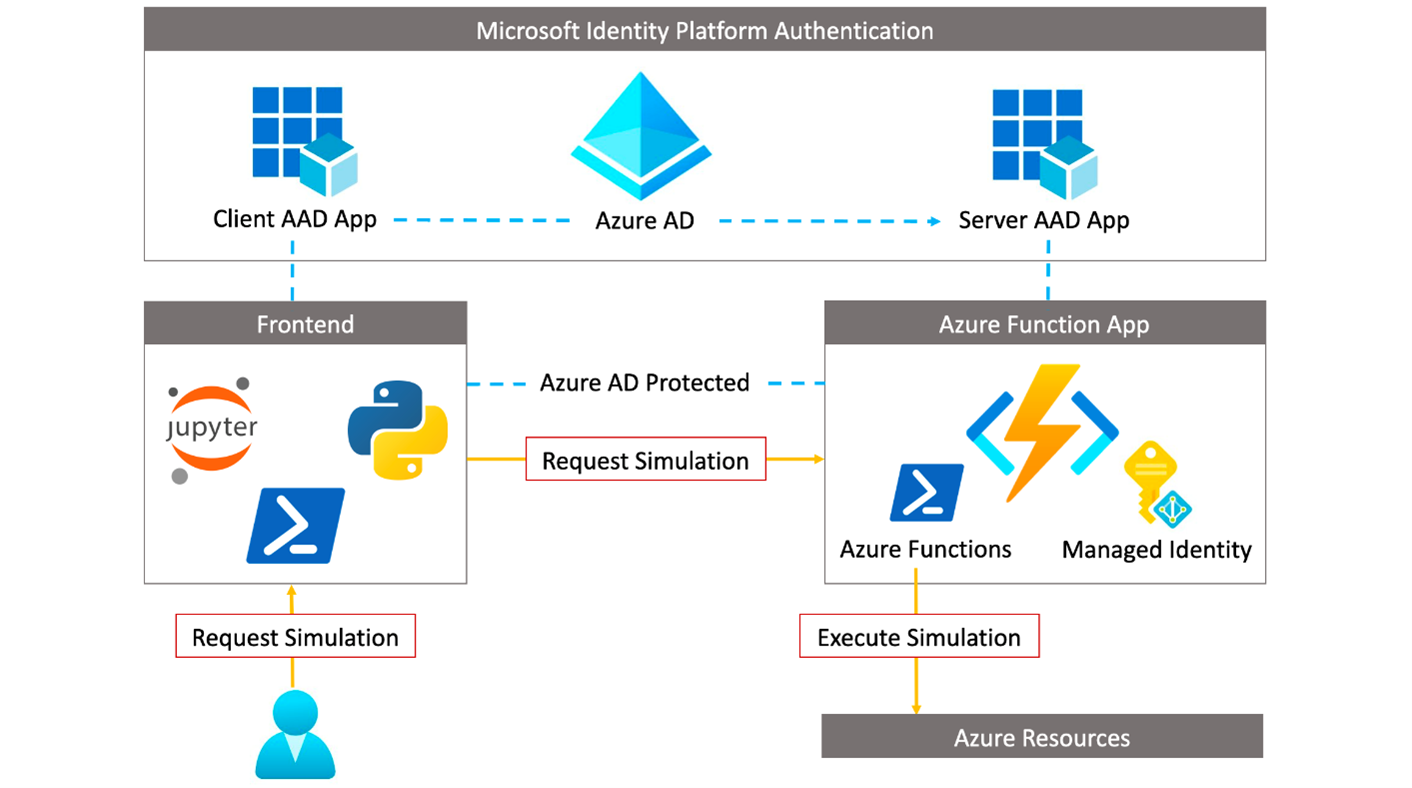
Cloud Katana is built on top of Azure Functions, Microsoft’s serverless computing solution. the idea behind Cloud Katana is to run “simulations” to test cloud security, as well as hybrid cloud security. The attack simulation is launched via PowerShell and YAML is used for logging.
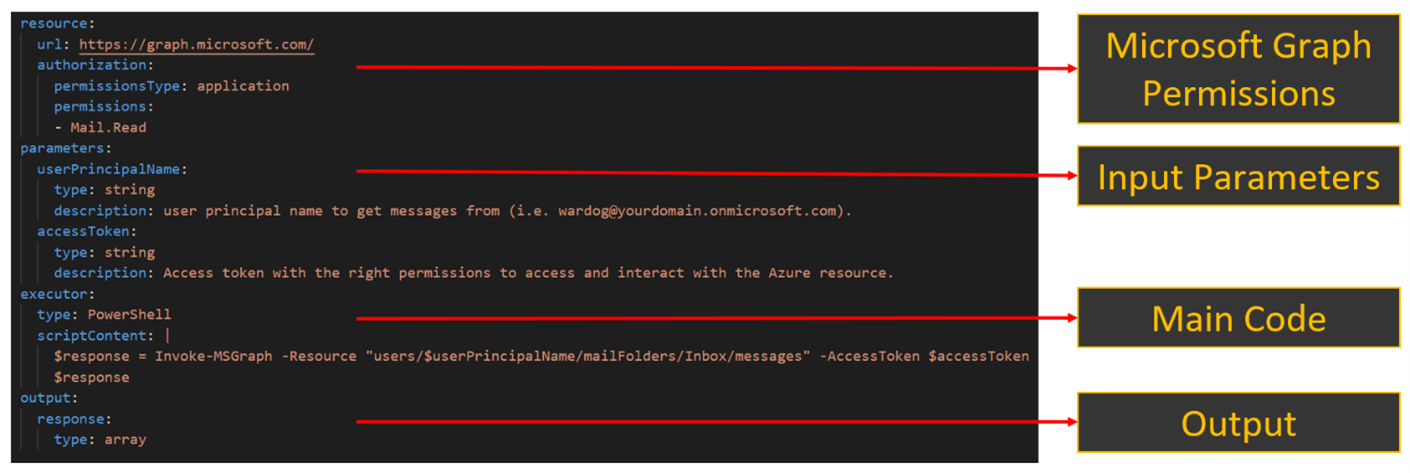
Each attack simulation is logged in a YAML-based format to aggregate metadata such as title, description, ATT&CK mapping, expected inputs and outputs, and even include prerequisites to ensure we have the correct permissions before running the simulation steps. This facilitates programmatically handling the operation of each record and automatically setting up a number of other resources.
The steps associated with the simulation are performed using “functions”, which are blocks of code called via HTTP requests. Azure Active Directory is used to connect to the Azure Functions service, and conditional access, multi-factor authentication and single sign-on can be set up for the person running the simulation.
Cloud Katana relies on the concept of Platform as a Service (PaaS) to provide a simplified and scalable event-driven solution without the worry of deploying and maintaining the underlying infrastructure used to perform the simulation.
Cloud Katana is not limited to testing the security of cloud services. Microsoft is also evaluating its use on locally based machines. Support for local-based machines involves using the Azure Application Services Hybrid Connect service, which uses “relay agents to expose services running on-premises to the public cloud in a secure manner,” Microsoft explains.
Cloud Katana was designed and developed based on the following principles.
- Serverless execution mode
- On-demand computing as a Web API
- YAML-based attack definitions
- Secure Authentication and Authorization
- Managed Identity Integration
- Fine-grained access control to Azure resources
- Programming-language-agnostic clients
- Cloud and local overlays
The project is currently hosted on the GitHub repository and interested developers can click on the link to find out more.