The Android malware “Brata” has received a series of updates that, in addition to stealing money from the bank accounts of infected Android devices, allow it to activate a “termination” switch: performing a factory reset to clean up the infected device.
“Brata” was first mentioned in a post by security firm Kaspersky, and the malware is mainly It was first mentioned in a [post] by security firm Kaspersky (), where the malware was mainly spread through Google Play, but also through third-party app markets, infected push notifications on websites, or messages delivered through tools such as WhatsApp or SMS.
At the time, Brata was targeting people with Brazilian bank accounts, but now it has made a comeback, and in addition to expanding the software’s scope of attack (it now attacks devices and bank accounts in other regions as well), its malicious attack features have been updated, the most important one being the ability to perform a factory reset on an infected device, erasing any traces left by the malware after an unauthorized bank transfer is attempted on the infected device.
Security firm Cleafy Labs was the first to report on this switch. In addition, Cleafy mentioned other features recently added by Brata, including: GPS tracking, improved communication with the control server, the ability to continuously monitor the victim’s banking application, and the ability to locate the location of the bank account, which can be roughly divided into three categories of variants based on the combination of different features.
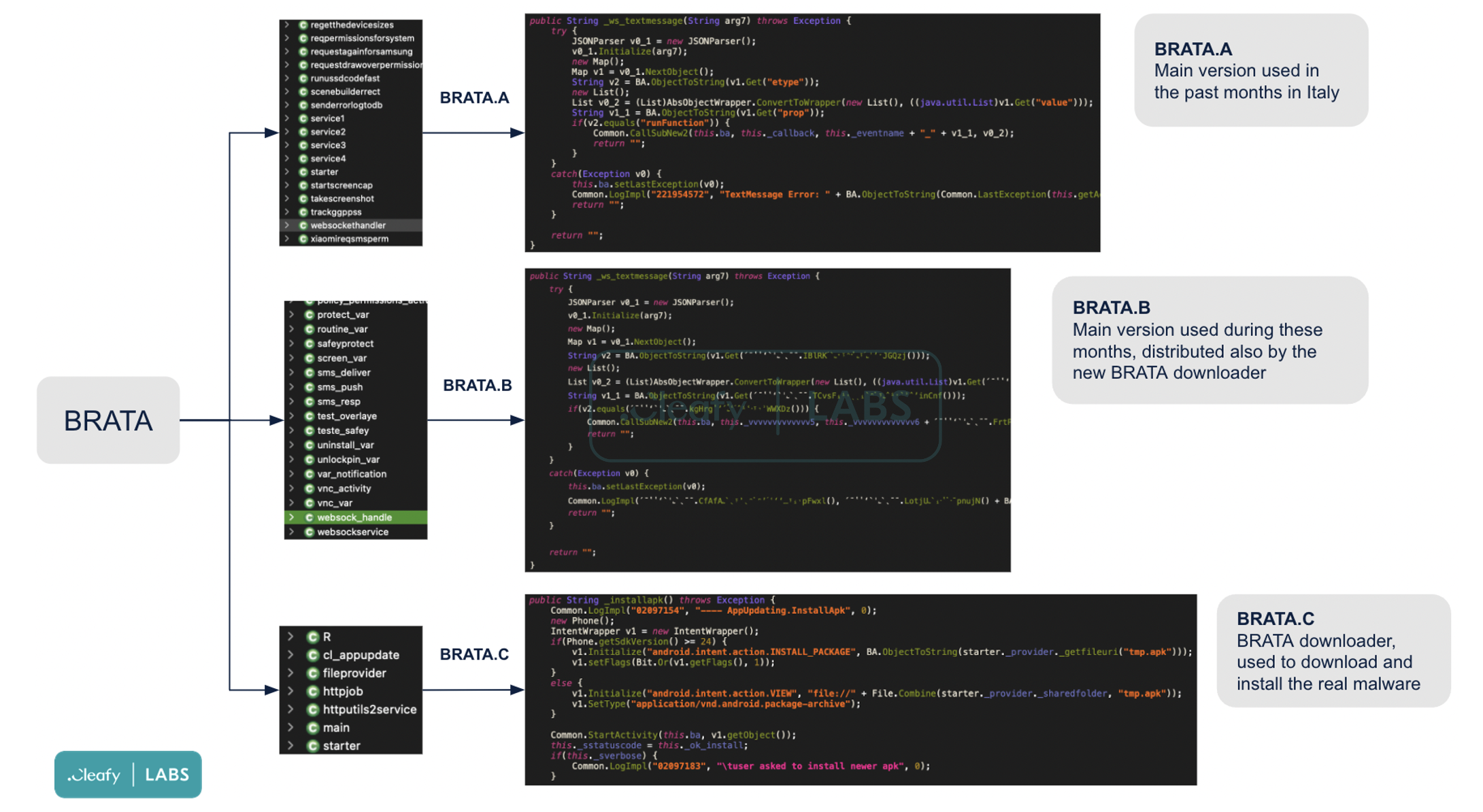
Brata is currently being distributed via phishing messages disguised as bank warnings, and its associated APP has not yet been found in major app stores.