1. A comparison of several common gateways
- Nginx, modular reverse proxy software, developed in C
- OpenResty, a Nginx-based web development platform that parses and executes Lua scripts
- Kong, an application of OpenResty, is an API gateway with API management and request proxy functions, using PostgreSQL storage
- APISIX, which replaces Kong’s PostgreSQL for Etcd, based on Nginx’s core library implementation
The advantage of APISIX is that it provides API management and extension capabilities, allowing the gateway to be configured and customized instead of just forwarding services. Compared to Nginx, APISIX uses dynamic routing, avoiding the risk of reloading after configuration. At the same time, APISIX supports more protocols such as HTTP(S), HTTP2, Dubbo, QUIC, MQTT, TCP/UDP, etc., providing a better usage ecosystem.

Above is the architecture of APISIX, where the data plane handles the client requests and the control plane manages the routes.
2. What problems APISIX can solve
- Edge routing
The number of access portal IPs exposed to the public by the server room is usually very small, but supports many services. For example, the access IP is 1.2.3.4, but provides access to a.domain.com, b.domain.com at the same time. This requires the use of edge routing, which will take access to different domains and forward them to different intranet addresses.
There are three ways to register edge routes in APISIX, dashboard, ingress-controller, and admin api.
- Basic gateway capability
The function of gateway is not limited to forwarding traffic, but more importantly, limiting traffic, fusing, etc.
APISIX has many built-in plug-ins that provide APM, logging, fusion, authentication, certificate management, fault injection, and other functions. It also supports drag-and-drop combination of new plug-ins and development of new plug-ins to meet business needs.
- Serverless
APISIX provides Serverless by means of plug-ins, and currently only supports Lua, but the combination of APIGateway + Serverless is very imaginative.
With Serverless, you can quickly provide a service-free API to the outside world, bond various services, and also provide functional services directly to the outside world.
- Grayscale release
Thanks to the control of the gateway layer, APISIX allows users to control the forwarding behavior of traffic by configuring weights, which can be used for grayscale distribution.
3. Installing APISIX on Kubernetes
3.1 Adding the Helm source
- Add the Helm source
- Find a Chart package
|
|
3.2 Installing APISIX
- Installing APISIX
|
|
- View the entrance address
The entry address here is the entry address of the backend service. If you are generating an environment, you should use the address provided by LoadBalancer.
- View apisix-admin interface key
|
|
The first key is admin and the second key is viewer. this key can be used to configure APISIX via the admin api, providing an entry point for other systems to integrate with APISIX.
3.3 Installing Dashboard
- Installing Dashboard
|
|
The default account is: admin The default password is: admin
- View Dashboard Access Portal
3.4 Installing ingress-controller
- Install ingress-controller
|
|
Here you will need to set the admin key obtained above, and in fact the ingress-controller also configures the route by calling the admin api.
4. Create service tests
As mentioned earlier, APISIX has three ways to configure routes via the admin api. Here we will verify the use of Dashboard and Ingress.
- Create a service
|
|
- Exposure Services
|
|
- View Services
4.1 Dashboard Configuration Routing
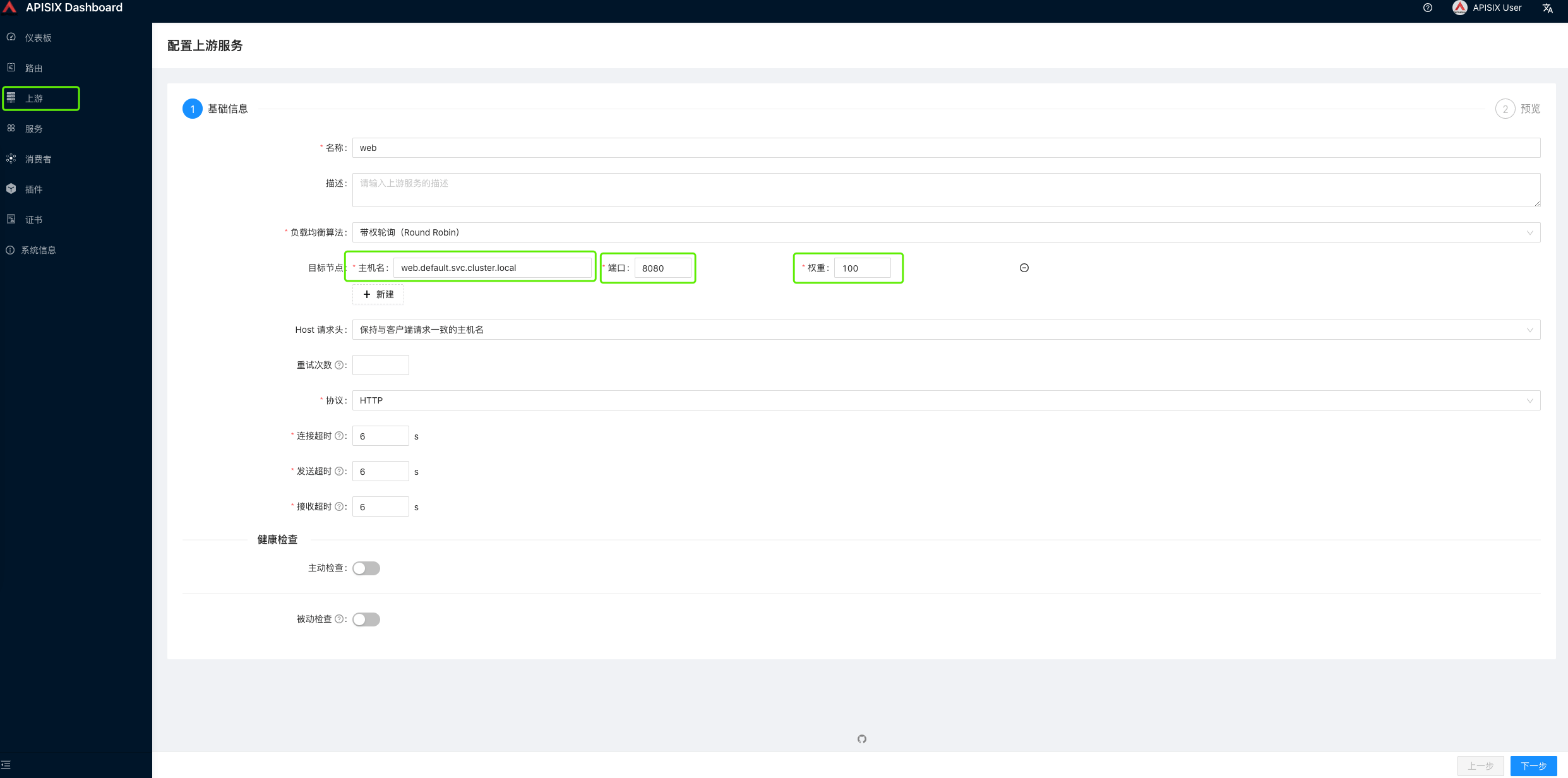
- Create a new upstream service
Here you need to fill in the cluster access address created above: web.default.svc.cluster.local
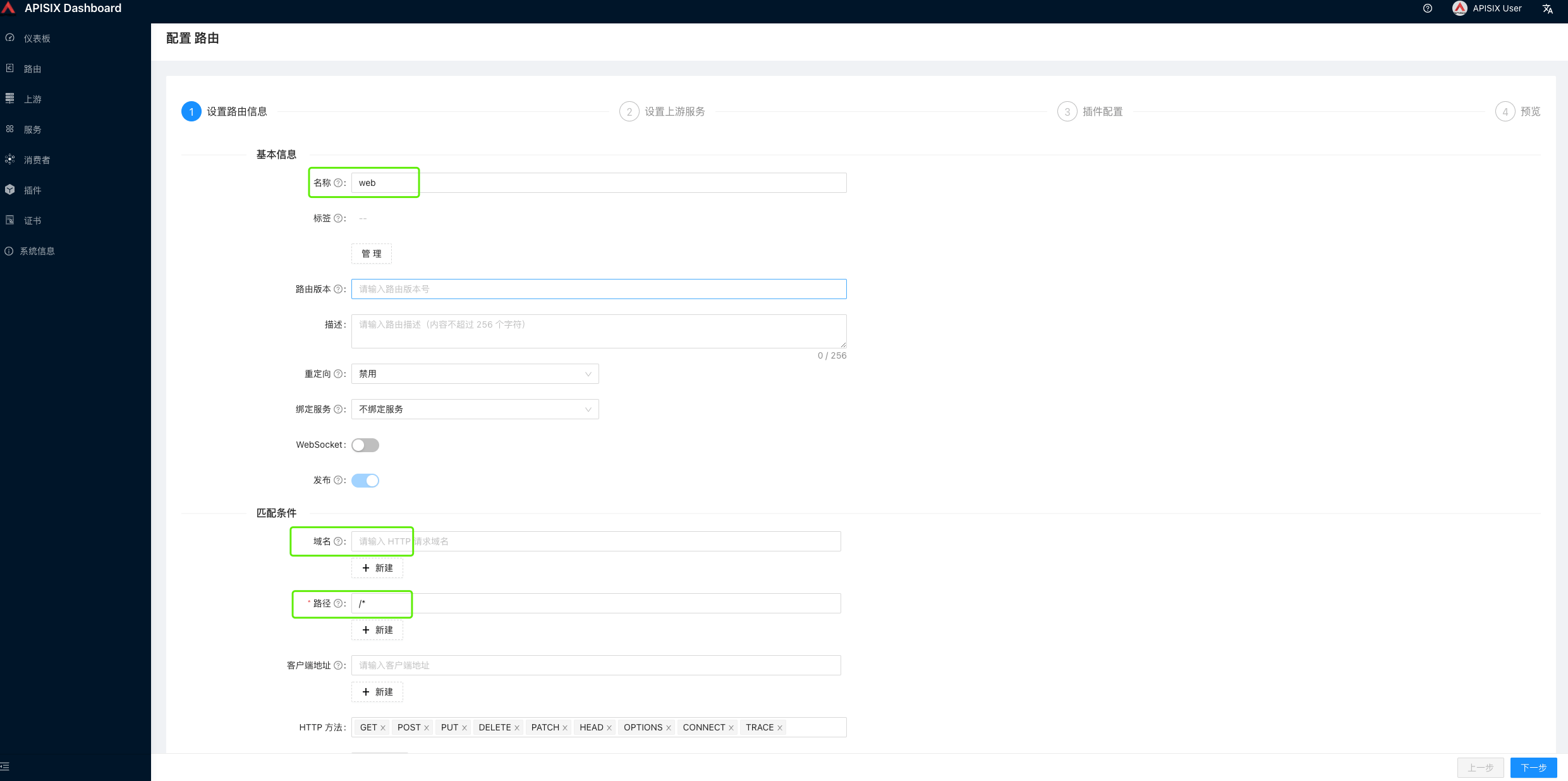
- Create a new route
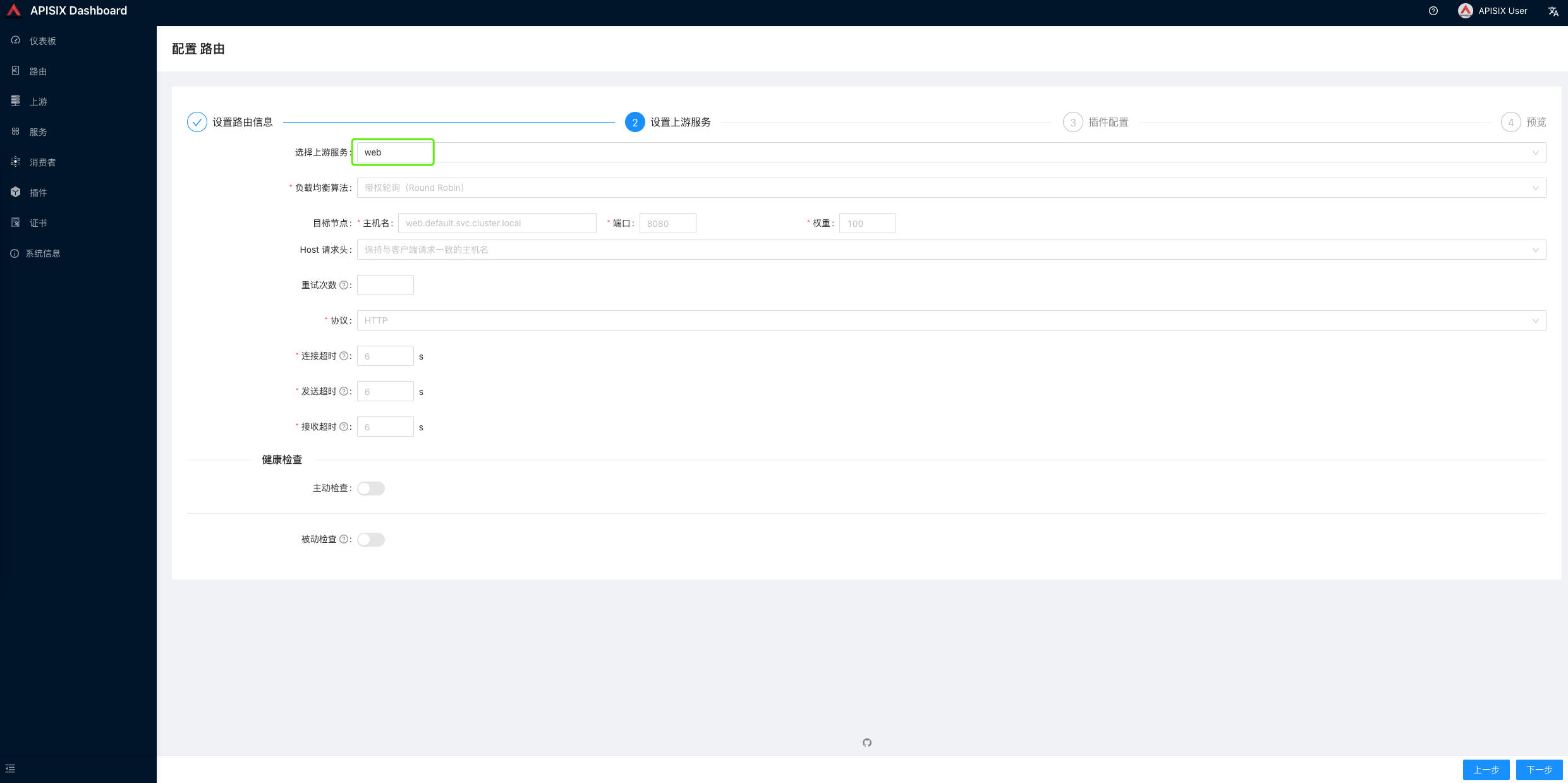
After clicking Next, select the service web created above and the relevant parameters will be populated automatically.
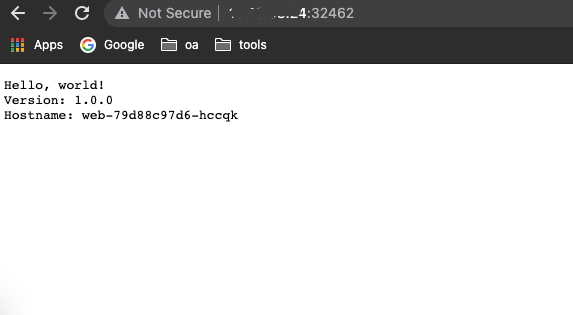
- Access test
4.2 Ingress Configuration Routing
- Create an ApisixRoute route
Although the ingress-controller component is deployed here, it is the ApisixRoute object that is created when it is used.
- Access test
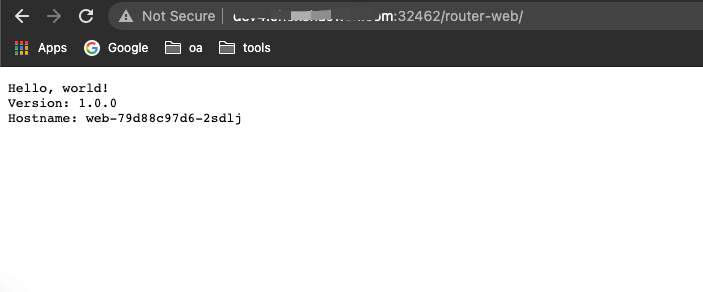
- View the created routes
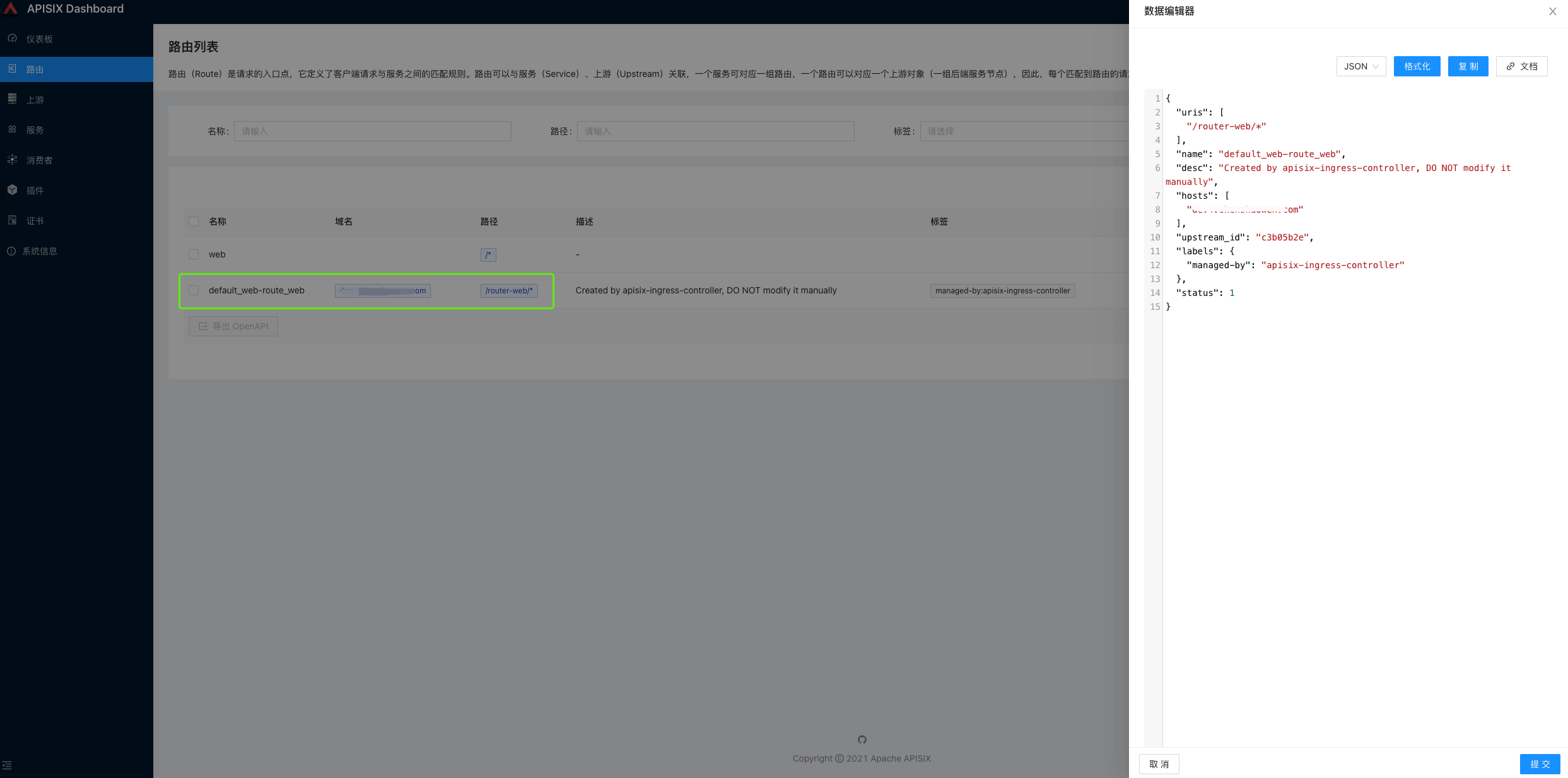
You can find that the route is managed by ingress-controller and should not be edited manually.
- View Services
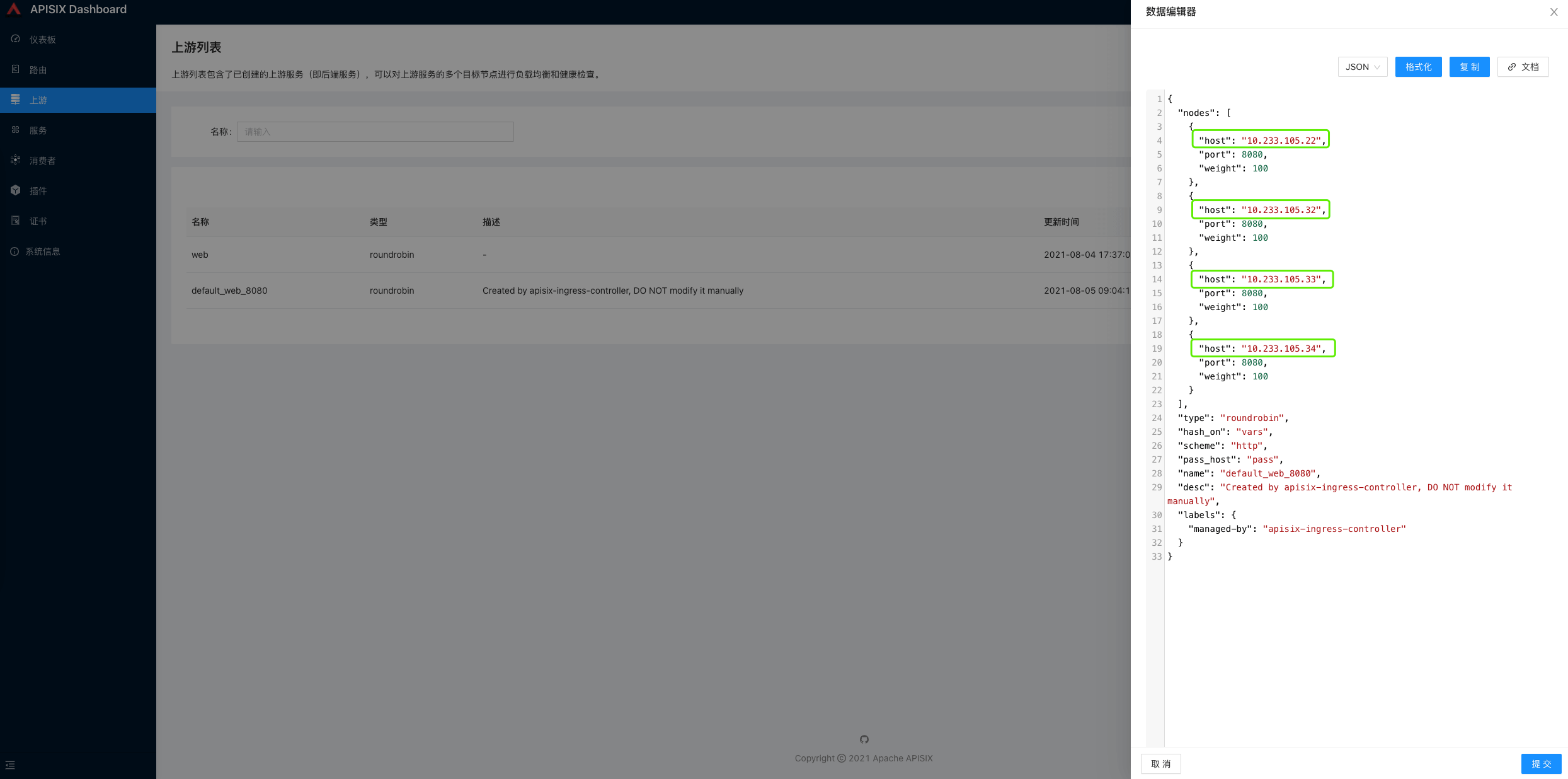
You can see that the service is mainly provided by four backends.
- View the IP of the Service Pod
|
|
APISIX will use the IP address of the Pod as the traffic backend directly without going through Service forwarding, which is different from Kubernetes’ service forwarding and load balancing mechanism.
5. Summary
In this article, we have briefly described the differences between several gateways, thought about what APISIX can do to help us solve our problems, and finally put it into practice on Kubernetes. The content is as follows.
- APISIX is an API gateway application implemented based on the Nginx network library, using Etcd as the storage backend
- APISIX can be used as an edge route, and its dynamic nature avoids the jitter caused by Nginx reloads.
- APISIX provides an admin api to manage routes, and there are three ways to configure it
- APISIX under Kubernetes skips the Kubernetes Service and forwards traffic directly to the Pod IP