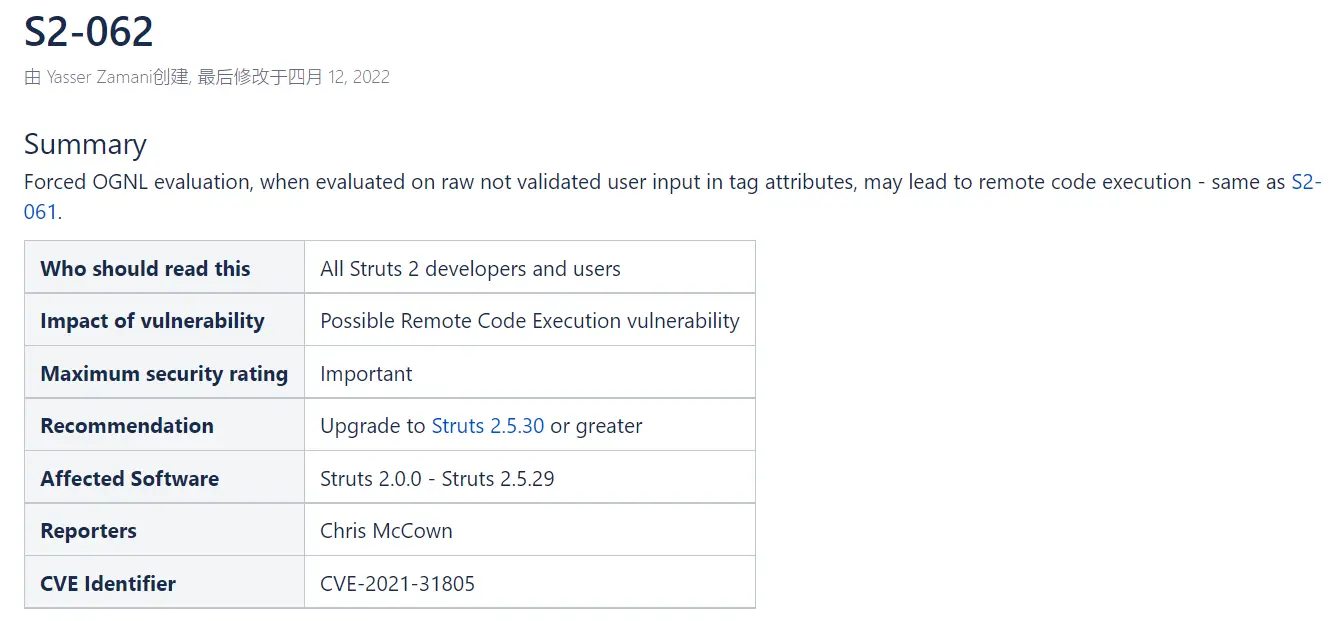
The Apache Software Foundation has issued a Security Advisory S2-062 to address a remote code execution vulnerability in Struts versions 2.0.0 through 2.5.29; an attacker could exploit this vulnerability to compromise an affected system. In response, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also issued a bulletin urging organizations to review the Apache bulletin and upgrade to the latest version of the Struts 2 patch as soon as possible.
The vulnerability is tracked as CVE-2021-31805 and is due to an incomplete fix for CVE-2020-17530 (S2-061) in 2020. This means that the vulnerability existed as early as 2020 and was thought to have been fixed at that time, but it turns out that the issue has not been fully resolved.
In 2020, GitHub researchers Alvaro Munoz and Masato Anzai of Aeye Security Labs reported an OGNL injection vulnerability in Struts 2 versions 2.0.0 - 2.5.25 under certain circumstances, as CVE-2020-17530, which received a score of 9.8 out of 10 on the CVSS severity scale. out of 10).
“If a developer uses the %{…} syntax for mandatory OGNL evaluation, some attributes of the tag can still perform double evaluation. Using mandatory OGNL evaluation on untrusted user input can lead to remote code execution and degraded security.”
Object-Graph Navigation Language (OGNL) is an open source Java expression language that simplifies the scope of expressions in the Java language. It is integrated into frameworks such as Struts2 and serves to access data; it has features such as type conversion, access to object methods, and manipulation of collection objects.
Although Apache addressed the vulnerabilities reported in 2020 in Struts 2.5.26, researcher Chris McCown found that the fix applied was incomplete. He reported to Apache that the “double-evaluation” issue can still be reproduced in Struts version 2.5.26 and later.
As a workaround, for its part, Apache recommends that developers avoid using mandatory OGNL evaluation in tag attributes based on untrusted user input, and/or upgrade to Struts 2.5.30 or later to check that expression evaluation does not lead to double evaluation. It is also recommended to follow the Security Guidelines for best practices.