Macvlan allows you to configure multiple virtual network interfaces on a single network interface of the host, these network interfaces have their own independent MAC addresses, or can be configured with IP addresses for communication. virtual machines or container networks under Macvlan are in the same network segment as the host and share the same broadcast domain. macvlan is more similar to Bridge, but because it eliminates the Bridge, it is simpler and more efficient to configure and debug. Macvlan is similar to Bridge, but it is easier and more efficient to configure and debug because it eliminates the presence of Bridge. In addition, Macvlan itself supports VLAN perfectly.
macvlan itself is a linxu kernel module whose function is to allow multiple MAC addresses to be configured on the same physical NIC, i.e. multiple interfaces, each of which can be configured with its own IP. macvlan is essentially a NIC virtualization technology (the biggest advantage is that it has excellent performance)
You can run lsmod | grep macvlan at the linux command line to see if the driver is currently loaded in the kernel; if not, you can load it by modprobe macvlan and check again. Kernel code path /drivers/net/macvlan.c
Bridge VS MACVlan
Bridge Mode
- Bridge is a Layer 2 device and is only used to handle Layer 2 communications.
- Bridge uses the MAC address table to determine how to forward frames (
Frame). - The Bridge learns the MAC address from the communication packets between hosts.
- It can be a hardware device or a pure software implementation (e.g.,
Linux Bridge).
Tip: Bridge may encounter Layer 2 loops, and STP can be turned on to prevent loops if needed.
MACVlan Mode
- Allows users to set multiple MAC addresses on the same physical NIC.
- The NIC with the MAC address set above is called the
sub interface; the physical NIC is called theparent interface. - The
parent interfacecan be a physical interface (eth0), a sub-interface of 802.1q (eth0.10), or abondinginterface. - Not only the MAC address can be set on the parent/sub interface, but the IP address can also be set.
- The
sub interfacecannot communicate directly with theparent interface(a VM or container with a sub interface cannot communicate directly with the host). - If the VM or container needs to communicate with the host, then an additional
sub interfacemust be created for the host to use. - The sub interface is usually named as
mac0@eth0for ease of differentiation.
Working Mode
Bridge Mode
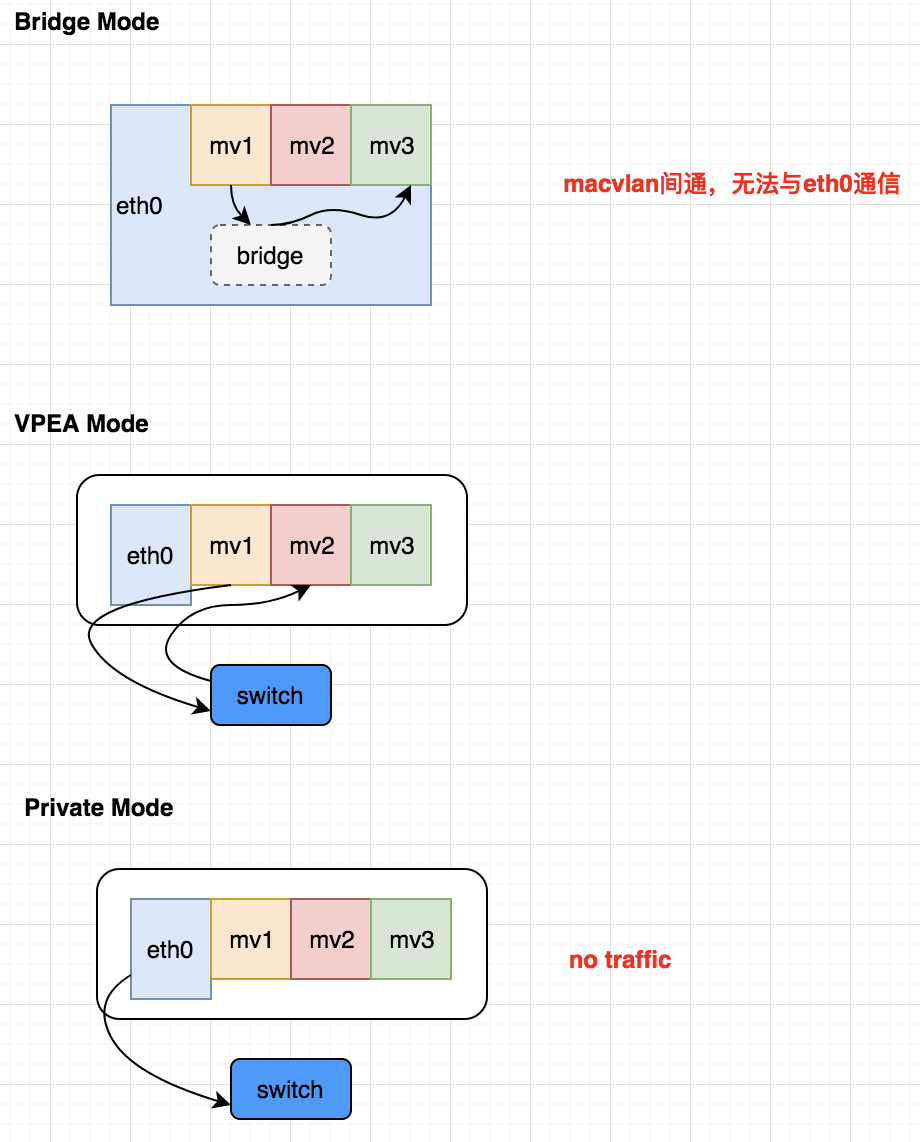
The macvlan interfaces belonging to the same parent interface are hooked up to the same bridge and can interoperate on layer 2 (none of the macvlan interfaces can interoperate with the parent interface)
VPEA Mode
Virtual Ethernet Port Aggregator, all interface traffic needs to go to the external switch to reach other interfaces
Private Mode
The interface only accepts messages sent to its own MAC address.
Passthru Mode
The parent interface is bundled with the corresponding MacVLAN interface. This mode allows each parent interface to be bundled with only one Macvlan virtual NIC interface, and the Macvlan virtual NIC interface inherits the MAC address of the parent interface.
Practices
The following experiment creates two macvlan interfaces and puts them into two netns; then verifies that the clients interoperate between these two macvlan ports.
First, use bridge mode to create two macvlan interfaces, whose parent interfaces are both eth0.
Check the results of the creation and note that each interface has its own mac address.
|
|
Create namespace
Insert the macvlan interface into namespace
Set NIC IP, set NIC UP status
Check the status of your network card.
|
|
net1 and net2 can’t ping through the host, ping themselves also can’t. 2 containers ping each other without problems
found that macv1 can not ping the host interface eth0 address.
But it is possible to ping the macv2 address.
Reference https://houmin.cc/posts/dccd6e26/